Blogs.

How abandoned cloud storage becomes an attack vector
For the full technical analysis, please visit the Eye Research website....


Log poisoning in AI agents: The OpenClaw case
For the full technical analysis, please visit the Eye Research website. AI...

Cyber Incidents in Europe 2026: Identity-based Attacks and the Impact of MDR
Cyber incidents across Europe are accelerating. They are happening more often,...

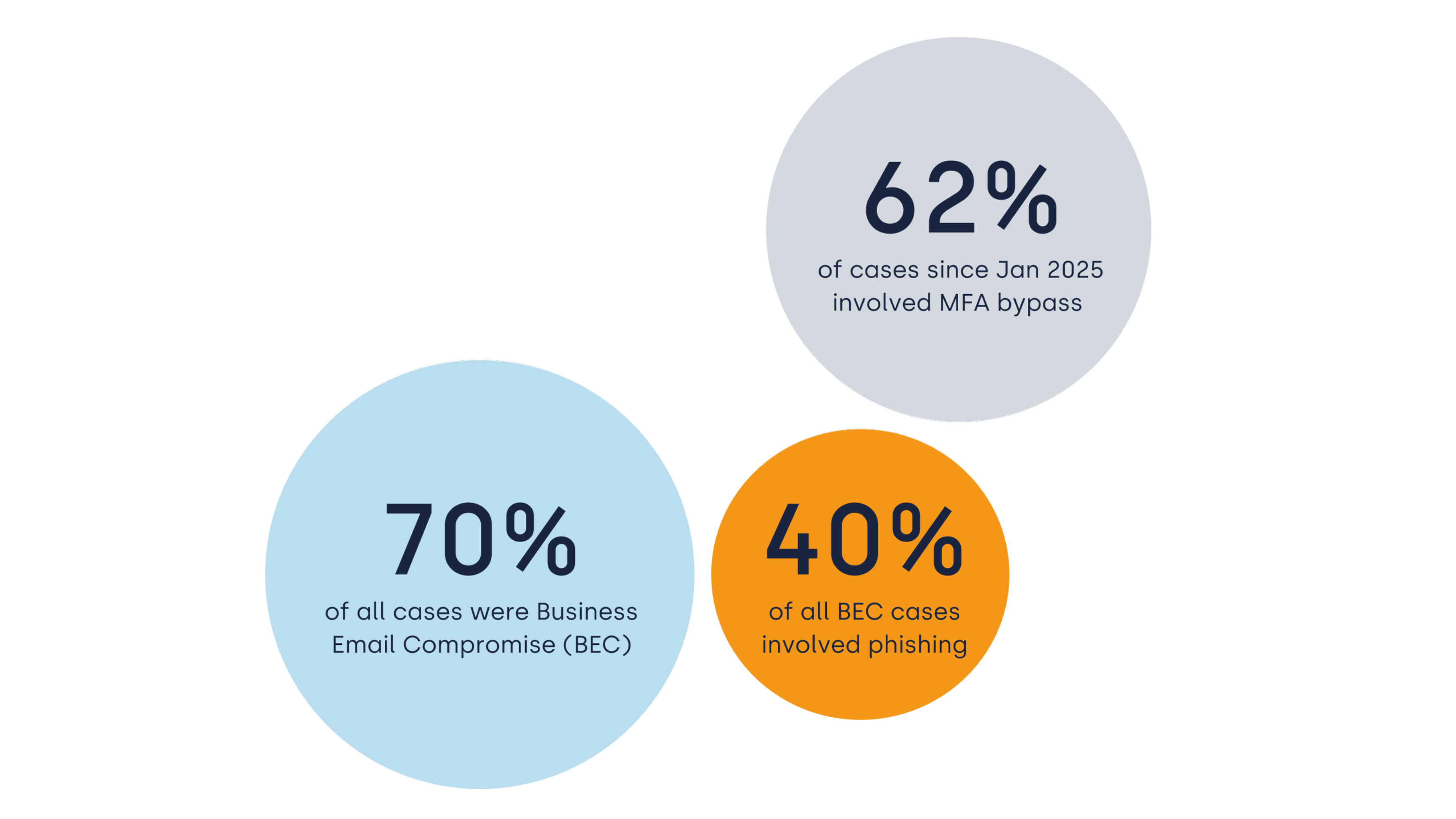
The State of Incident Response 2026: Insights from 630 Investigations
Eye Security analysed 630 anonymised cybersecurity incidents across Europe...
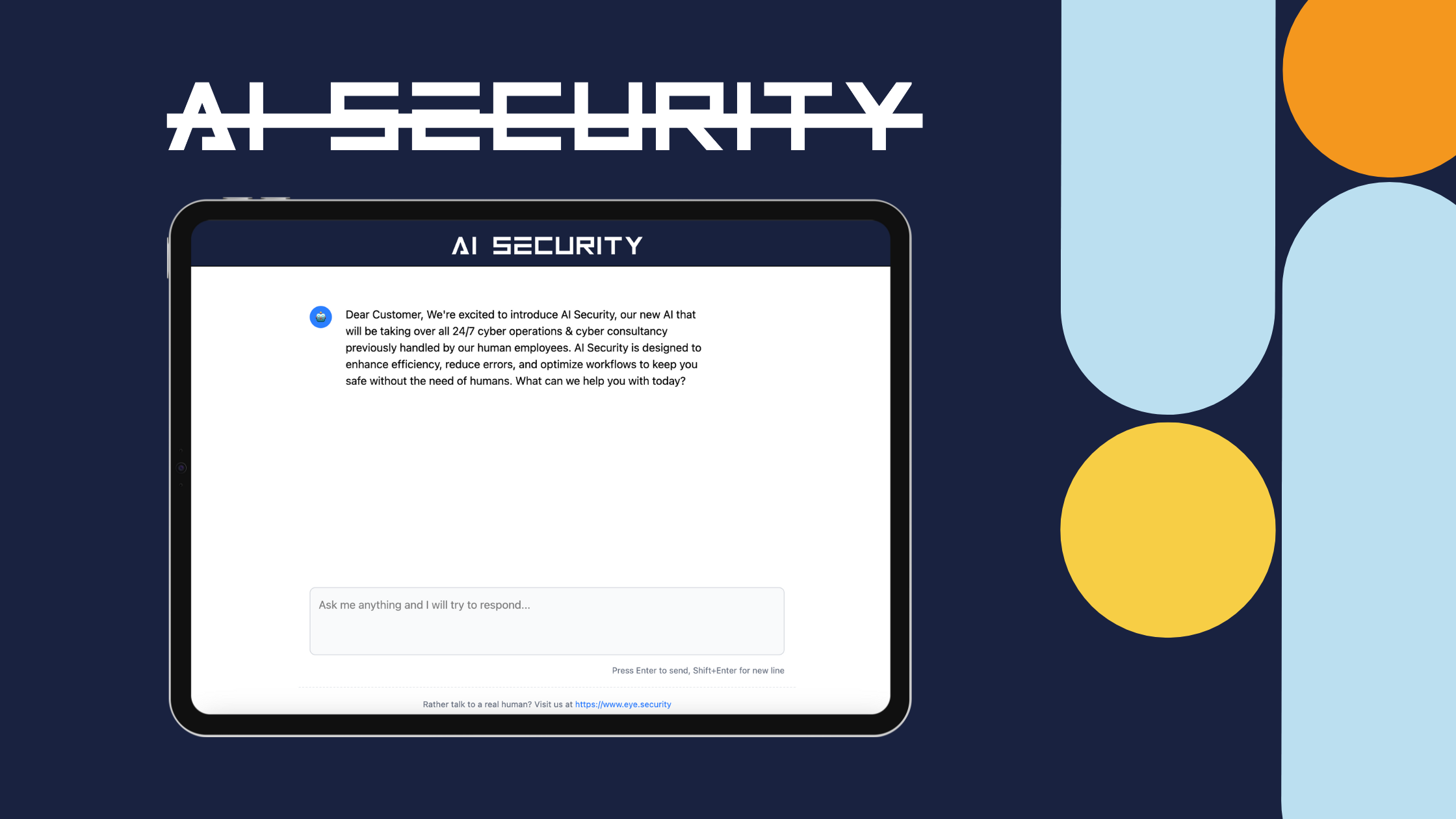
From Helper To Risk Factor: Why AI Canvases Deserve Executive Attention
Eye Research demonstrated that a shared AI canvas can convincingly imitate...


AI Agents in Cybersecurity: What’s Real, What’s Hype, and What's Next
Artificial intelligence is everywhere in cybersecurity conversations right now....

The Cyber Threat Landscape 2026: Building Resilience, Acting Fast
Cyber defence is entering a race measured in minutes, not days. As we move into...

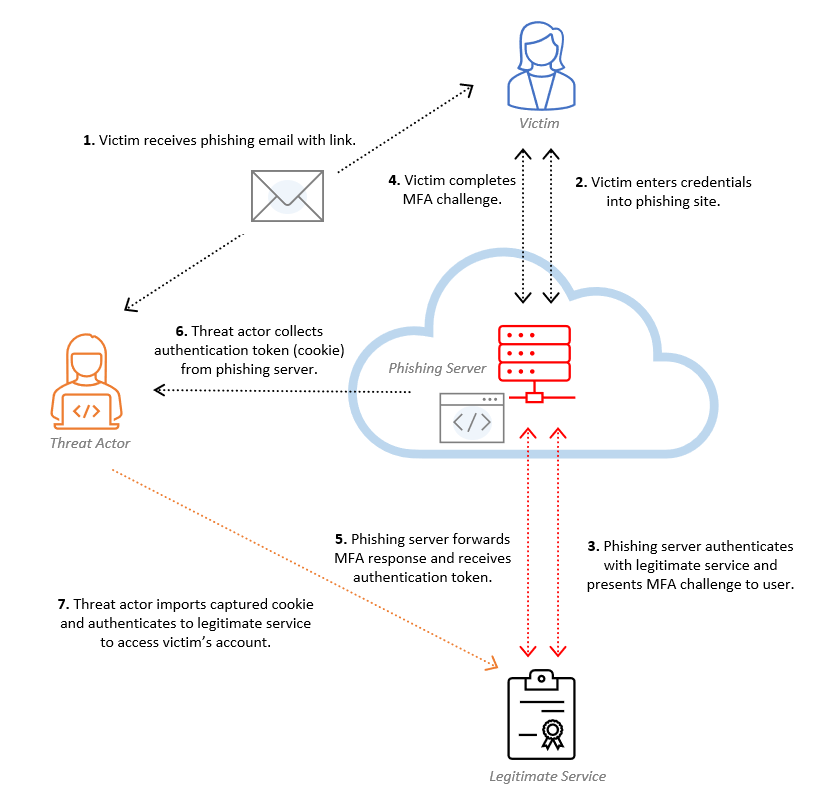
Microsoft 365 AitM Phishing Protection: Free Browser Extension
Adversary-in-the-Middle (AitM) phishing is a rapidly growing threat that can...
Insights from the SOC: Why Analysts Still Matter in the Age of AI
Every week, vendors announce new AI tools promising autonomous defence and...
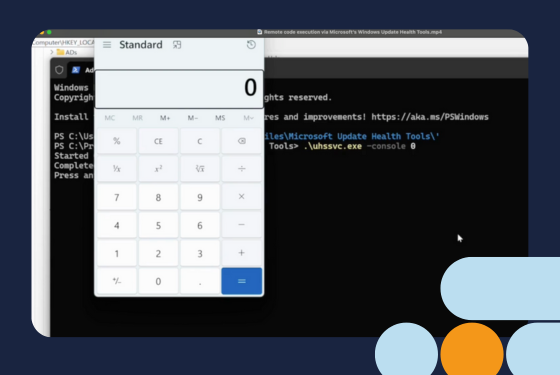
Remote code execution via Microsoft’s Windows Update Health Tools
For readers who want the full technical analysis, the detailed research blog is...

Battling Shadow AI: A Practical Tool for CISOs
Generative AI is transforming how businesses operate. Tools such as ChatGPT,...


Top Cyber Threats in Logistics and How to Defend Against Them
For decades, transport and logistics operators have focused primarily on...
When Business Email Compromise Nearly Costs a Million: An Incident Response Story
Business Email Compromise (BEC) remains one of the most damaging yet...

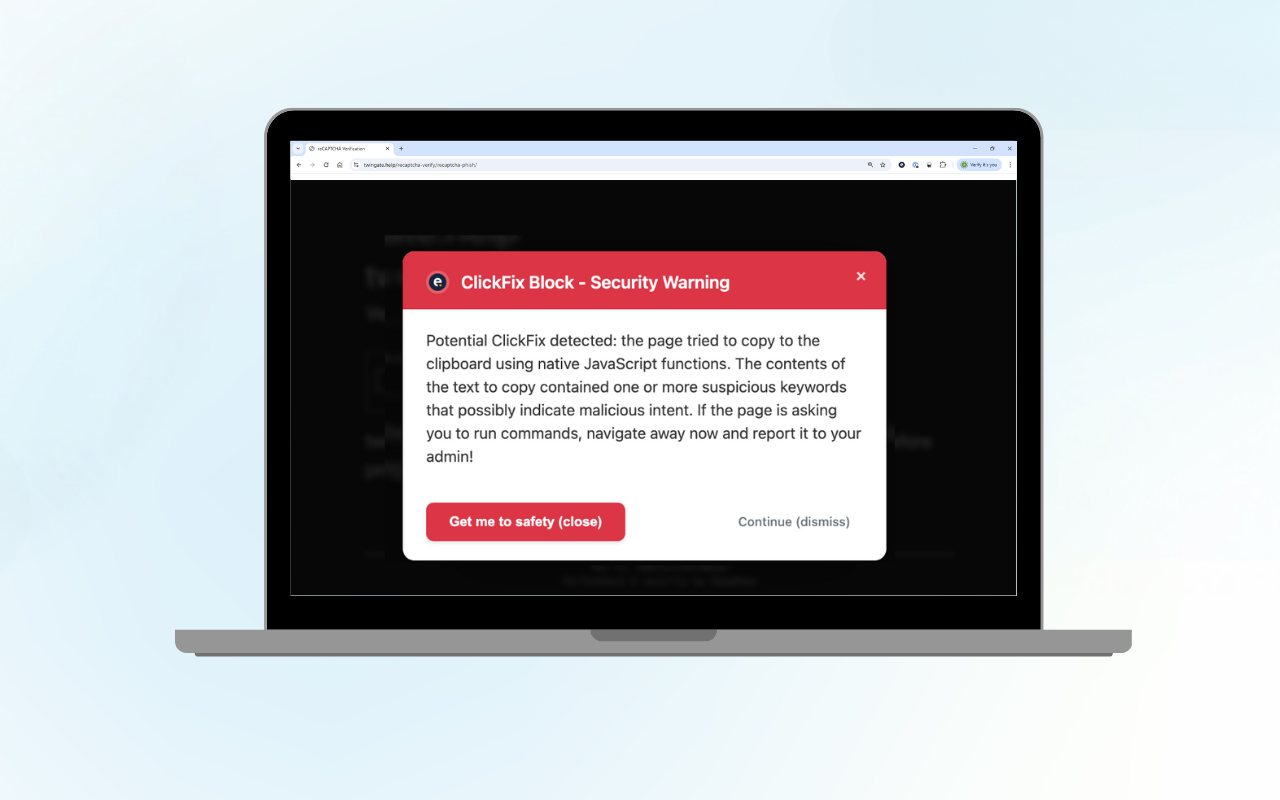
ClickFix Block: Protect Your Organisation from Fake CAPTCHA Attacks
Curious about the technical details? Read our technical blog on ClickFix Block....

Uses of AI in Enterprise Cybersecurity: Risks, Opportunities, Strategies
To fully unlock the potential of AI systems in cybersecurity, organisations...

Dual-use AI in Cyberattacks: How LLMs Are Reshaping the Threat Landscape
The malicious use of AI is evolving, making attacker tactics increasingly...

Hours from shutdown: How a Logistics company escaped ransomware just in time
This is a real incident Eye Security investigated at Move Intermodal. The...

Cybersecurity in transportation and logistics: inside the sector’s risks
Over the past five years, cybersecurity incidents have risen 48%, with the...

Eye Security Uncovers Actively Exploited Zero-Day in Microsoft SharePoint (CVE-2025-53770)
On the evening of July 18, 2025, Eye Security identified active, large-scale...
Brute Force Attack on SSLVPN Leads to Stealthy Network Intrusion
Attacks do not always start with malware or flashy exploits. Sometimes, all it...
Inside a Ransomware Attack: What a Real-World Incident Can Teach Us
“All systems went dark. We are locked out of everything. We don’t know how far...

Retail Giants Breached: What the M&S, Harrods & UNFI Attacks Mean for Your Cyber Defences
A surge of high-impact cyberattacks is shaking the retail sector, exposing...
The Eyes Behind Eye Security: Why People Matter in Cyber Security
A message from Piet Kerkhofs, CTO & founder of Eye Security...


Sneaky 2FA: Use This KQL Query to Stay Ahead of the Emerging Threat
At Eye Security, we constantly seek out new threats and detection methods to...


Top 5 Cyber Threats Manufacturers Face in 2025
Cyber attacks can be devastating to manufacturers. They disrupt supply chains,...
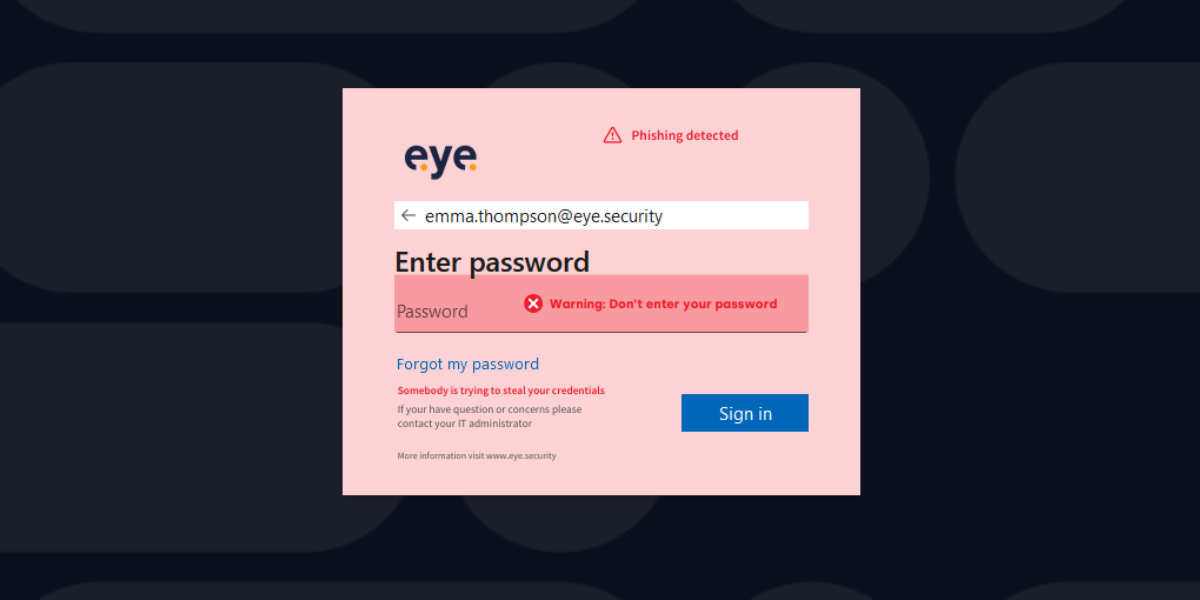
Microsoft 365 Credential Theft? Here’s a Free Anti-Phishing to Bolster Your Defences
Credential phishing is a constant threat. And Microsoft 365? Prime target. It's...
Manufacturing and Cybersecurity: What Are the Challenges?
Manufacturing companies form the very foundation of the global economy....

EDR vs NDR: Why Endpoint Security Has a Clear Advantage
Choosing the right cybersecurity tools can be challenging in a crowded...
Investigation of an 8Base Ransomware Attack Uncovers Surprising Insights
Almost every engagement of the Eye Security Incident Response team provides new...

Business Email Compromise: Fifteen Steps to Reduce the Risk
Business email compromise (BEC) is a concept that first appeared around 2013...

A new paradigm to extinguish cyber risk for good: 24/7 protection connects with cyber insurance
...

Eliminating cyber risk for your clients together
Businesses built on partnership In the relatively short time we’ve been in...
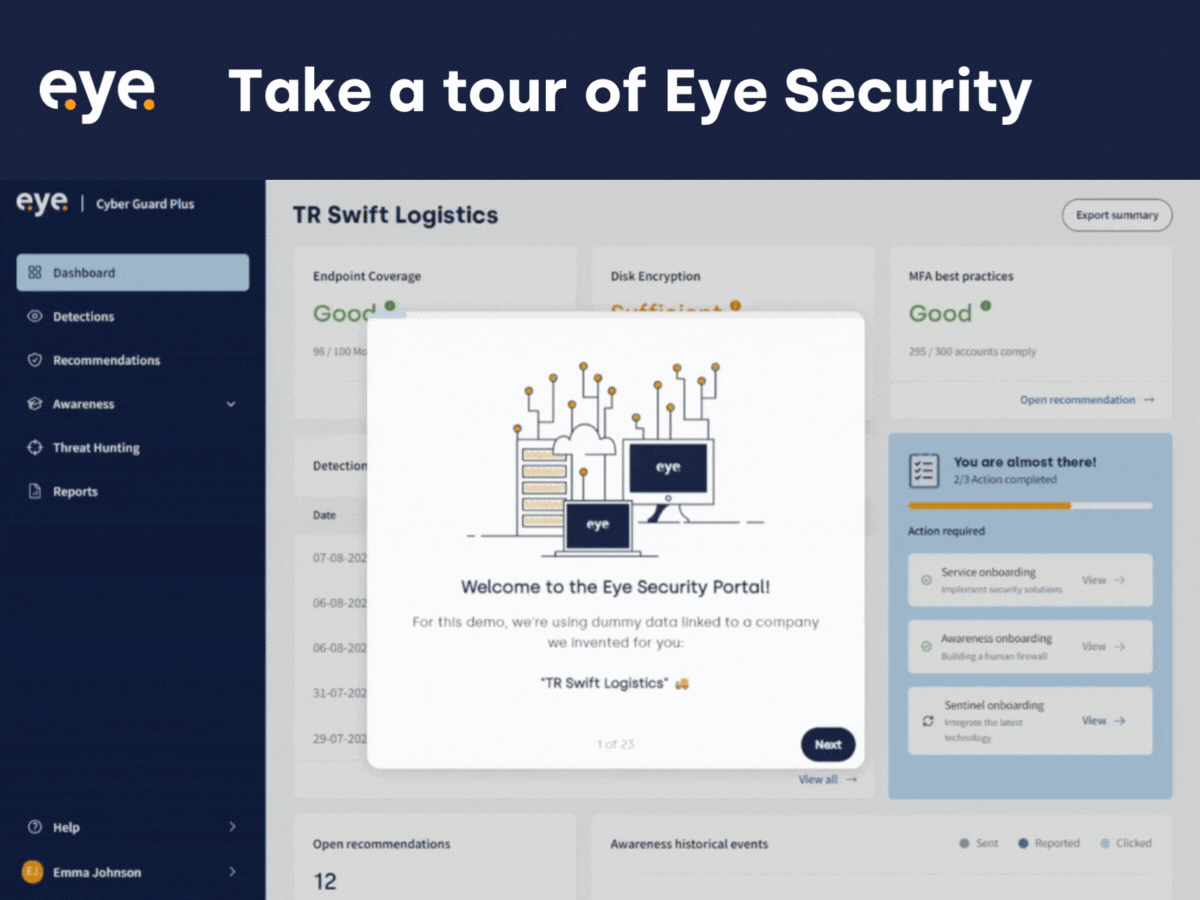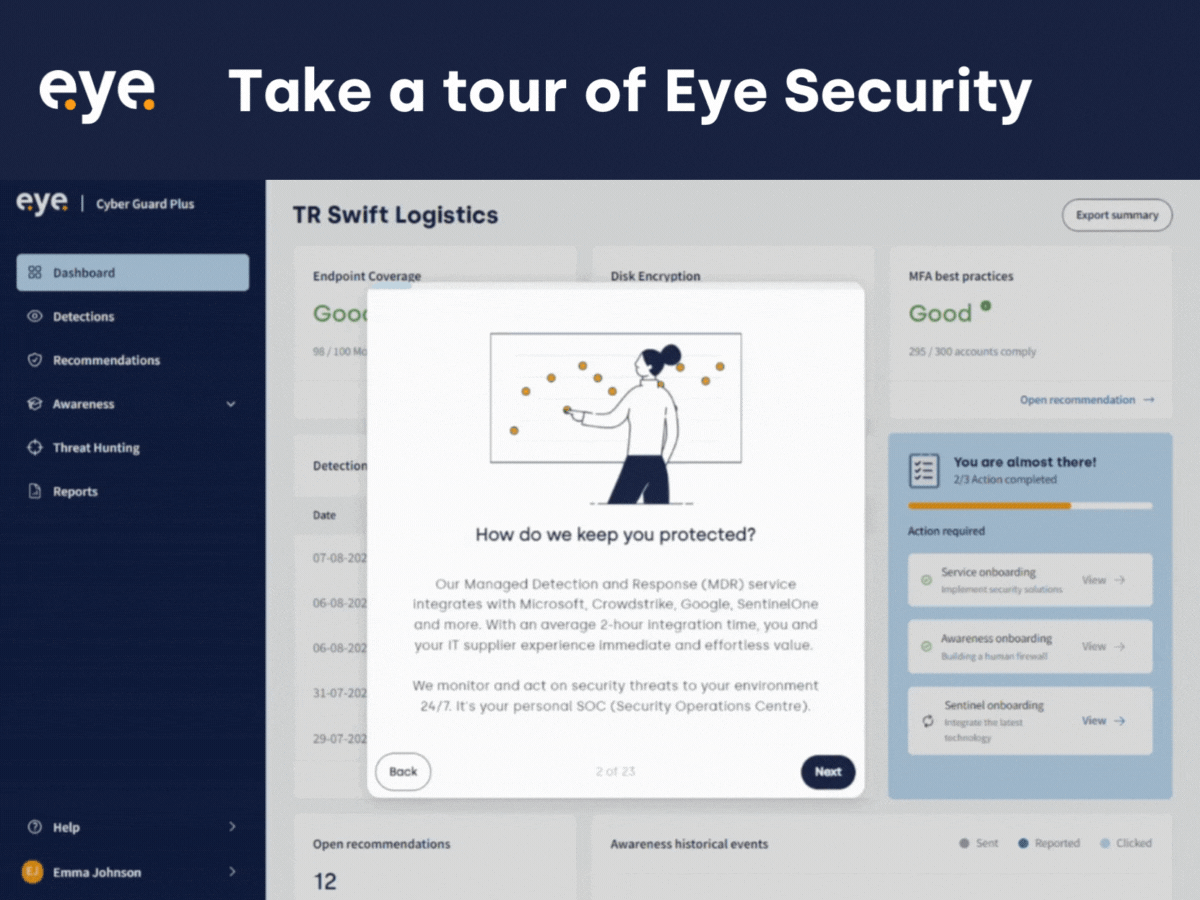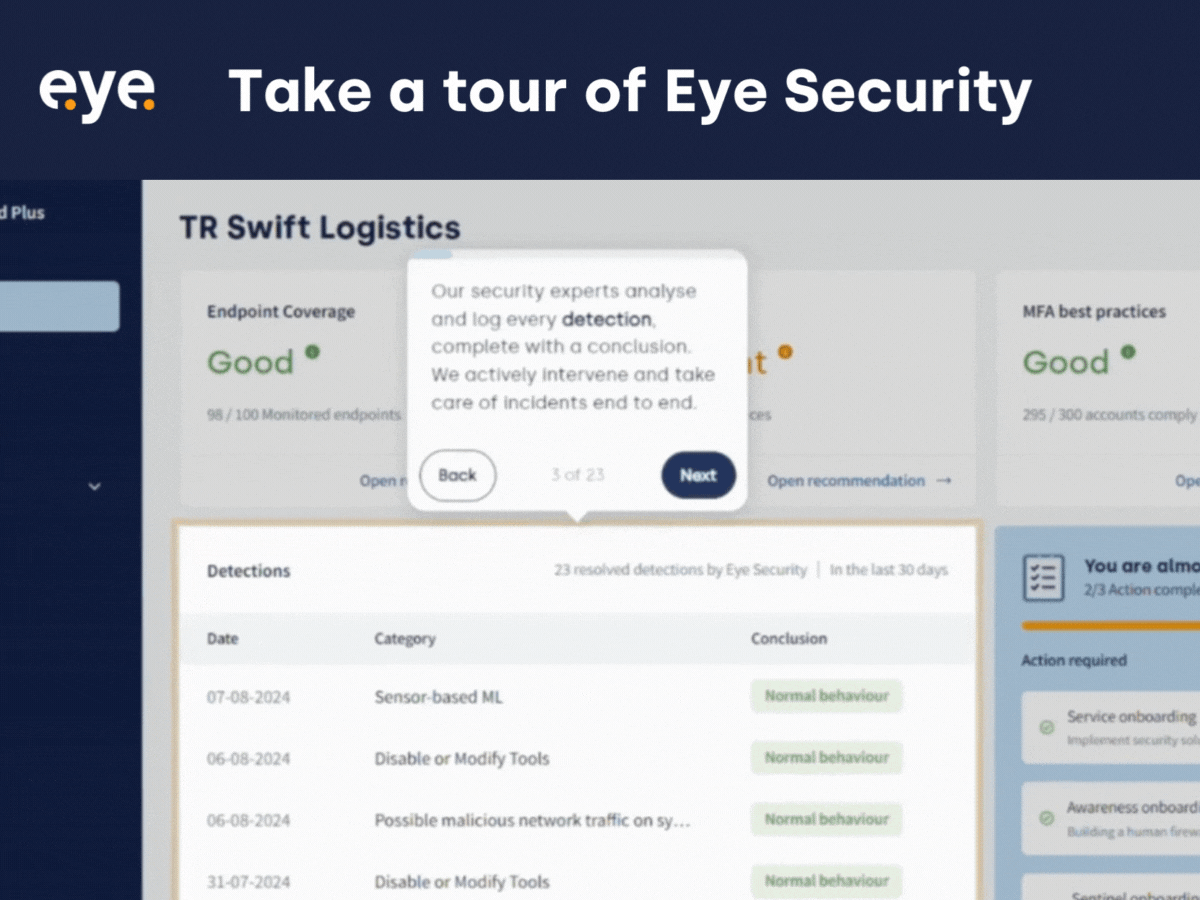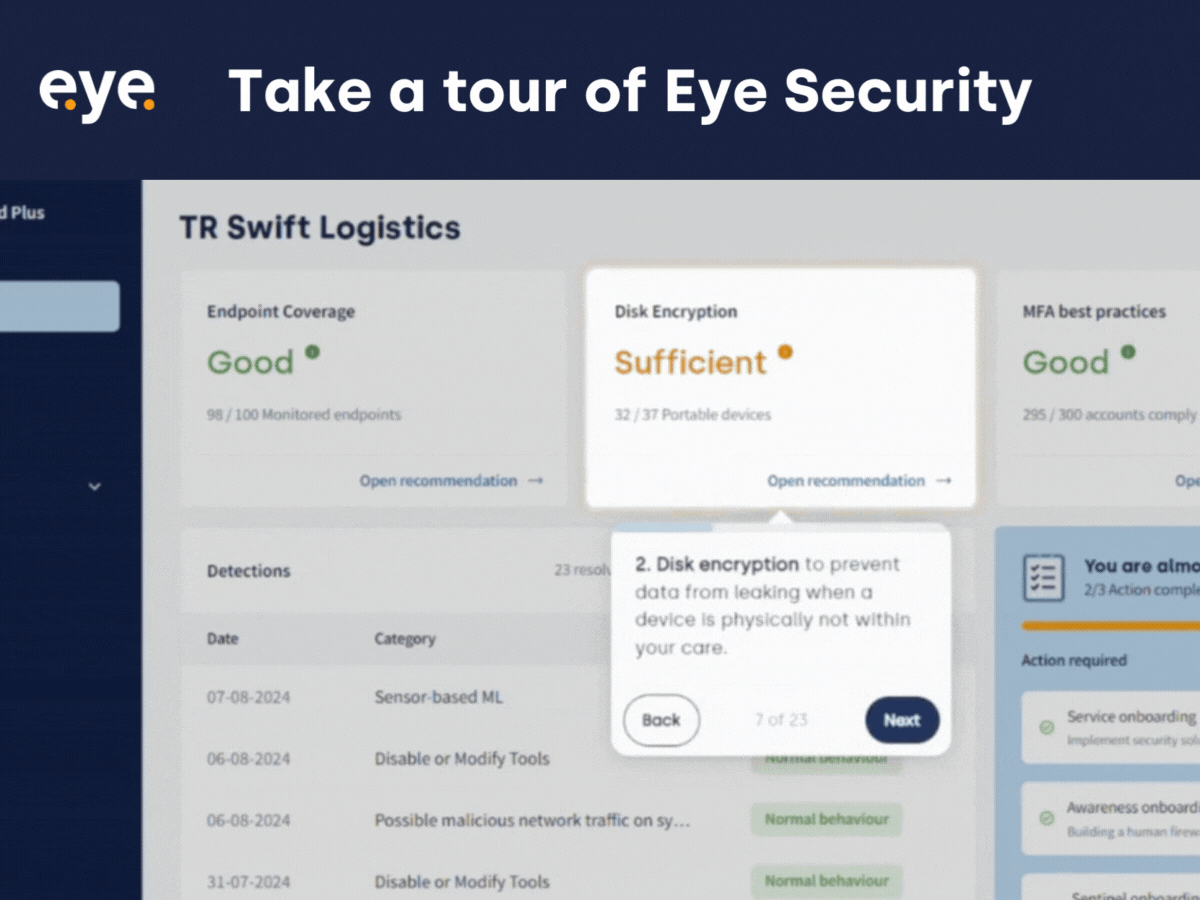
Product Update: Demo Portal
In this blog, we sit down with Anne Postma, our Product Manager, to discuss the...

Product Update: Vulnerability & Threat Hunting
In this blog, we interview Robbin Begeer, Product Manager at Eye Security,...
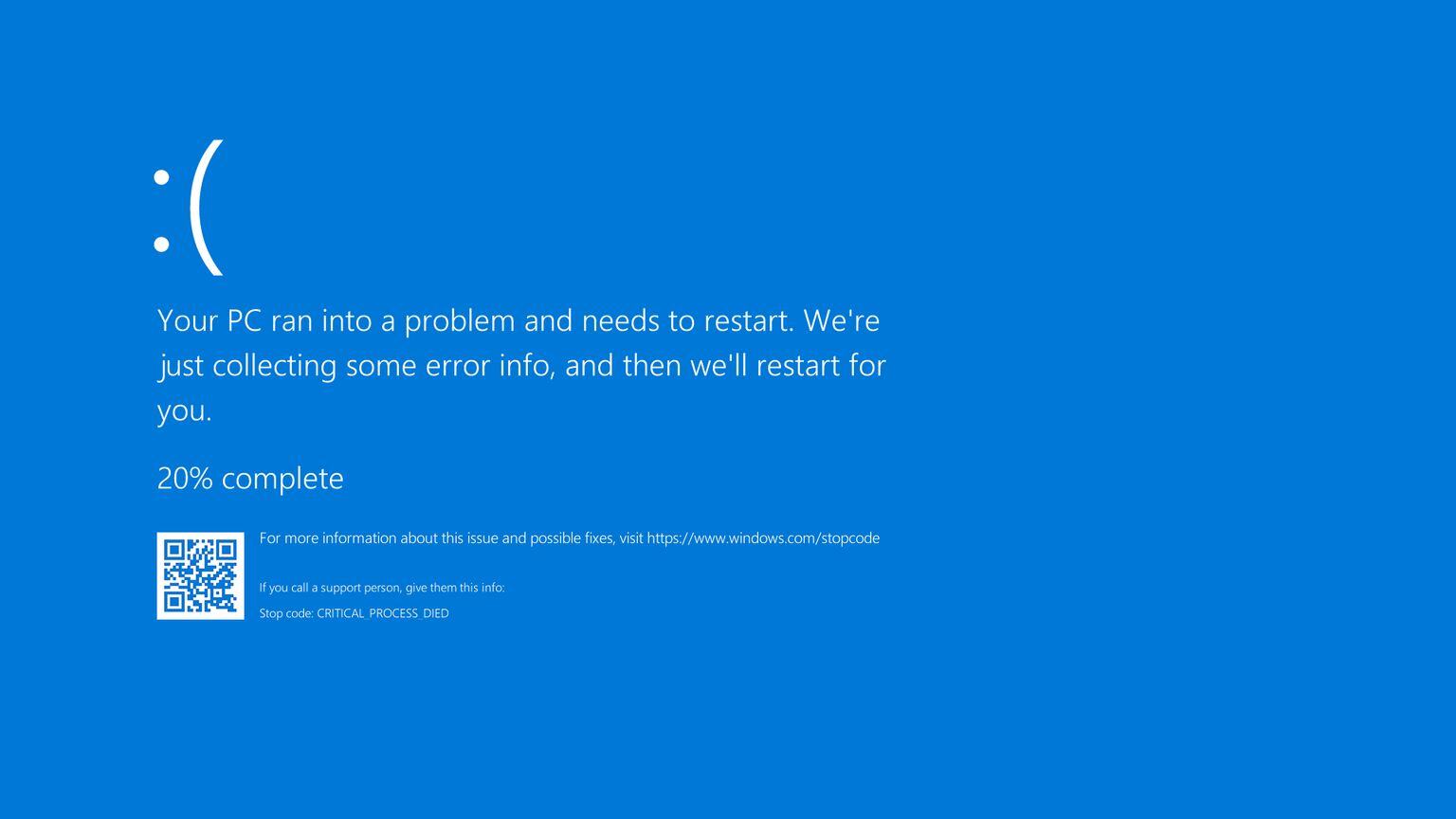
CrowdStrike Falcon and Microsoft blue screen issue updates
Last updated: July 30th at 00:00 CEST In this blog, we provided real-time...


NIS2 Directive Overview: In-depth look at Articles 21 and 23
While many EU countries are still working out the specifics of implementing the...

NIS2: How the New EU Cyber Law Protects Your Business
Cyber attacks are now big business – but they’re impacting smaller companies....


NIS2 EU: Top 3 Cyber Laws and Their High-Level Definitions
Cybersecurity compliance can seem daunting. With so many new regulations coming...

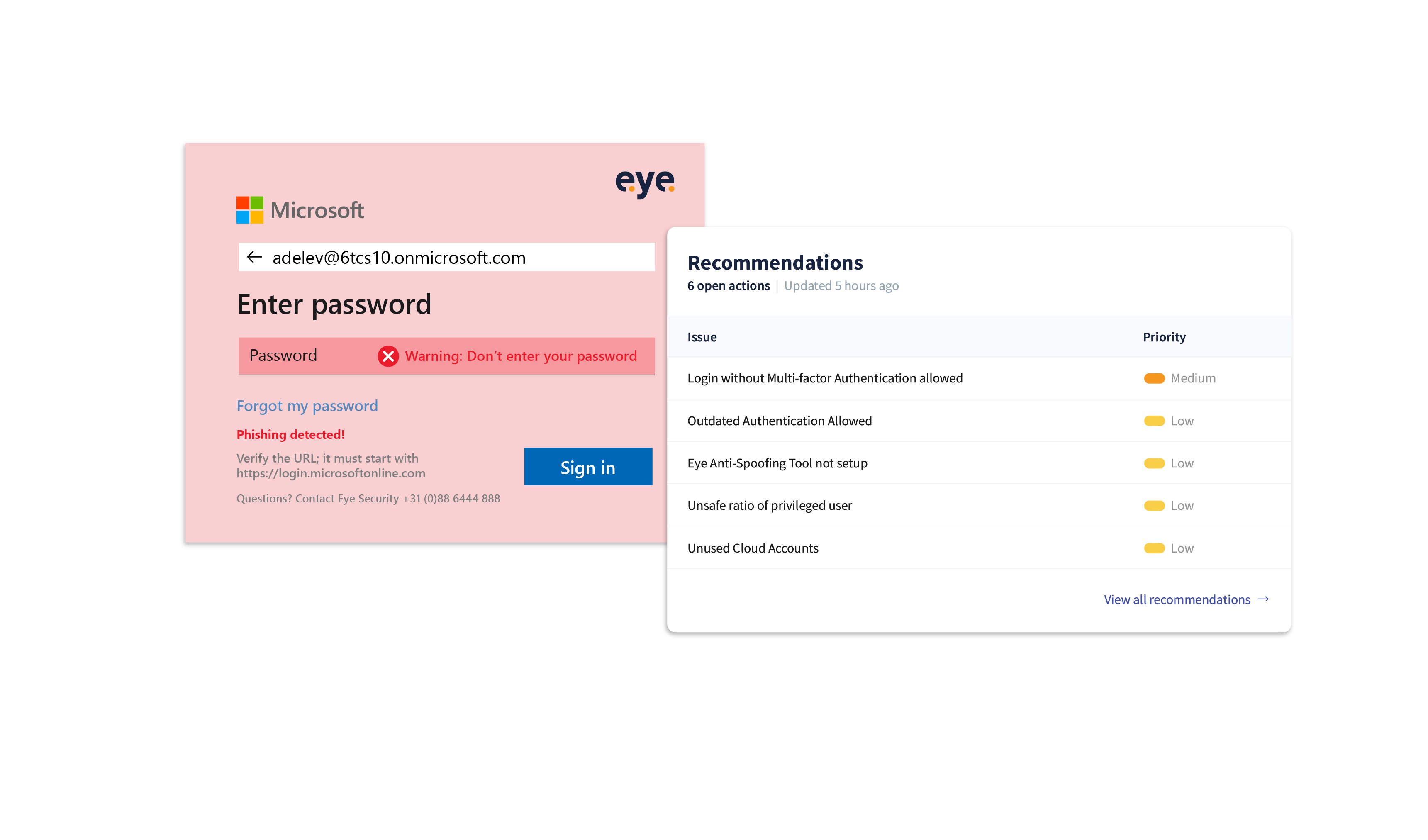
Empowering security: the battle against Login Spoofing
Introduction Battling cyber-crime can sometimes feel like an endless tennis...
A Conti-nuous issue
Introduction In this blog, we shed light on our findings during a forensic...


A case of ransomware, resolved
...

Logistics cybersecurity in 2024: Hello new growth! Hello new risks...
Sustainability. Growth. Digitalisation. These are the words everyone's using...
How to defend against EvilProxy when a phishing attack strikes
Here at Eye Security, we have observed a disturbing increase in security...


How we discovered outdated Windows Servers
Introduction Managing servers is the process of taking care of computer systems...

The story of a real vishing attack: detailed incident walkthrough
Introduction In this article, we'll cover the following: Context on vishing...
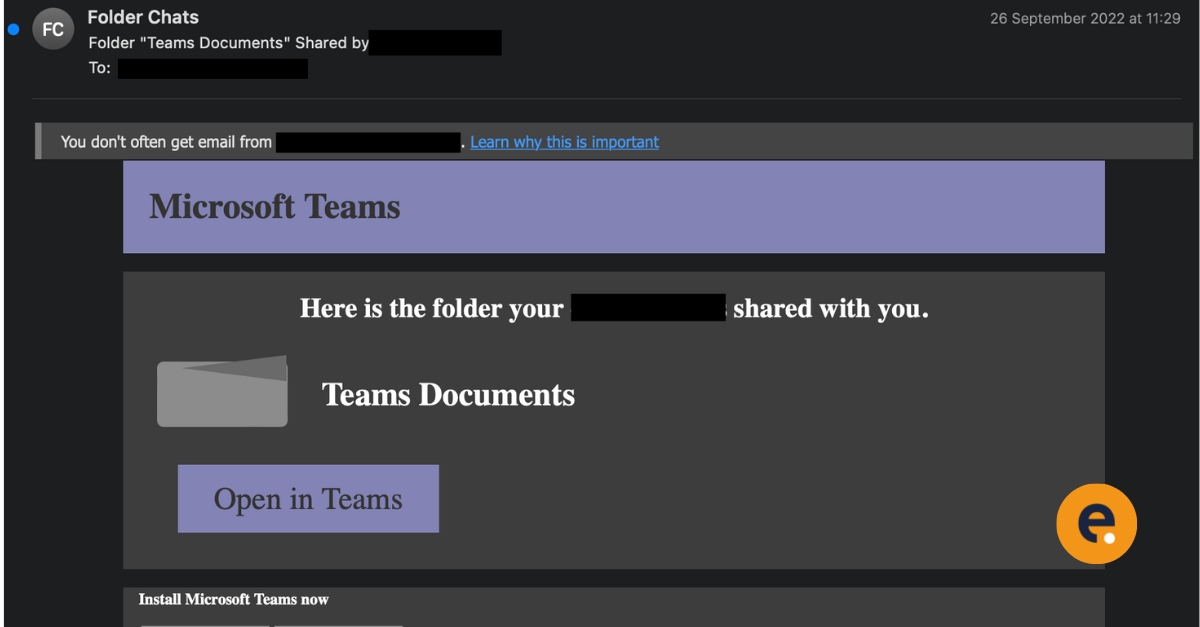
Microsoft Teams Phishing: How to Stop The Rising Phishing Threat
Introduction Around mid-September, our Security Operations Centre (SOC)...

Mitigating Cyber Threats with Risk Intelligence
What is Risk Intelligence - and how can it help you? Business leaders...


Hunting for You and Eye #1
Eye Security's ongoing hunt for cyber threats provides valuable insights into...

The silent crisis: IT burnout due to increased cybercrime
Employee absenteeism is rising among IT managers and employees, as are burnout...

Security Alert: Critical Geoserver Vulnerabilities
We want to bring your attention to a critical vulnerability in GeoServer that...


NIS2: how will it be transposed in European countries?
The NIS2 Directive is the latest European cybersecurity regulation, aiming to...

When it comes to cybersecurity, insurers set the bar high
The insurance market is now aware that cyber risk is difficult to manage and...


European Union working on new security directive
The impact of the new 'cybersecurity' directive, NIS2, on insurers Although the...
Cyber insurance: your safety net in an increasingly risky world
To minimise the impact of a cyber incident, preventive security measures must...

What is the chance of getting hacked? Eye Security: 1 in 5
In recent years, we have seen an increasing number of cyber attacks on...

6 Cybersecurity Resolutions for 2023 – And How to Implement Them
The new year is a good opportunity for companies to break bad habits -- such as...

Antivirus is not enough to protect your business - here is why
Many antivirus software providers claim that their product will protect you...
Large scale phishing campaign quickly utilises Legacy Authentication before Microsoft disables it
Security Specialists from Eye Security have observed a rather large phishing...

WinRS and Exchange, a sneaky backdoor
How it started ? On the 10th of May around lunch, our Security Operation Centre...

Are new employees the weakest link in your organisation?
We have all been there: starting a new job can be very overwhelming. There are...


Log4j Critical Updates by Eye CERT
Introduction Attackers are actively exploiting a remote code execution...

5 tips to secure your company for free
No matter how big or small your company is, everyone has crown jewels: crucial...

How does machine learning in cybersecurity help detect threats?
Machine learning makes an important contribution to cybersecurity by...

What is social engineering and how do I protect my company against it?
Social engineering is the temptation of people to reveal sensitive information...

What is a Zero Day? How to Ensure Zero Day Protection for Your Company
A zero day is an unresolved vulnerability in software that puts end users at...

You can protect yourself against supply chain ransomware – here's how
Still in shock, the media is suggesting that there is little that can be done...

Who is responsible for the damage in a cyber attack?
In 2021, the Central Netherlands court made a striking decision. Bol.com and...

What you want to know from your IT supplier in the field of security
Within SMEs there is still the impression that they are not of interest to...

Breaking ABUS Secvest internet-connected alarm systems (CVE-2020-28973)
ABUS Secvest is a wireless alarm system that is marketed at consumers and small...

We help Hospitals - Together against Corona
Introduction NATO, Red Cross, UN and Interpol warned in March 2020 about...


When the data doctor makes you ill (but we decrypt his ransomware)
What happened? Recently, we were contacted by Aon Nederland Cyber Solutions,...

Undocumented user account in Zyxel products (CVE-2020-29583)
TL;DR: If you have a Zyxel USG, ATP, VPN, ZyWALL or USG FLEX you should update...
