Blogs.

Microsoft 365 AitM Phishing Protection: Free Browser Extension
Adversary-in-the-Middle (AitM) phishing is a rapidly growing threat that can...

Microsoft 365 AitM Phishing Protection: Free Browser Extension
Adversary-in-the-Middle (AitM) phishing is a rapidly growing threat that can...
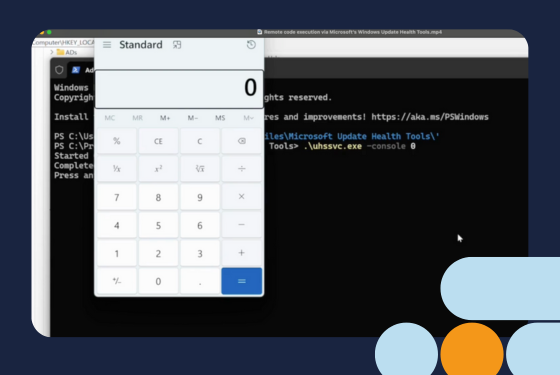
Remote code execution via Microsoft’s Windows Update Health Tools
For readers who want the full technical analysis, the detailed research blog is...

Battling Shadow AI: A Practical Tool for CISOs
Generative AI is transforming how businesses operate. Tools such as ChatGPT,...

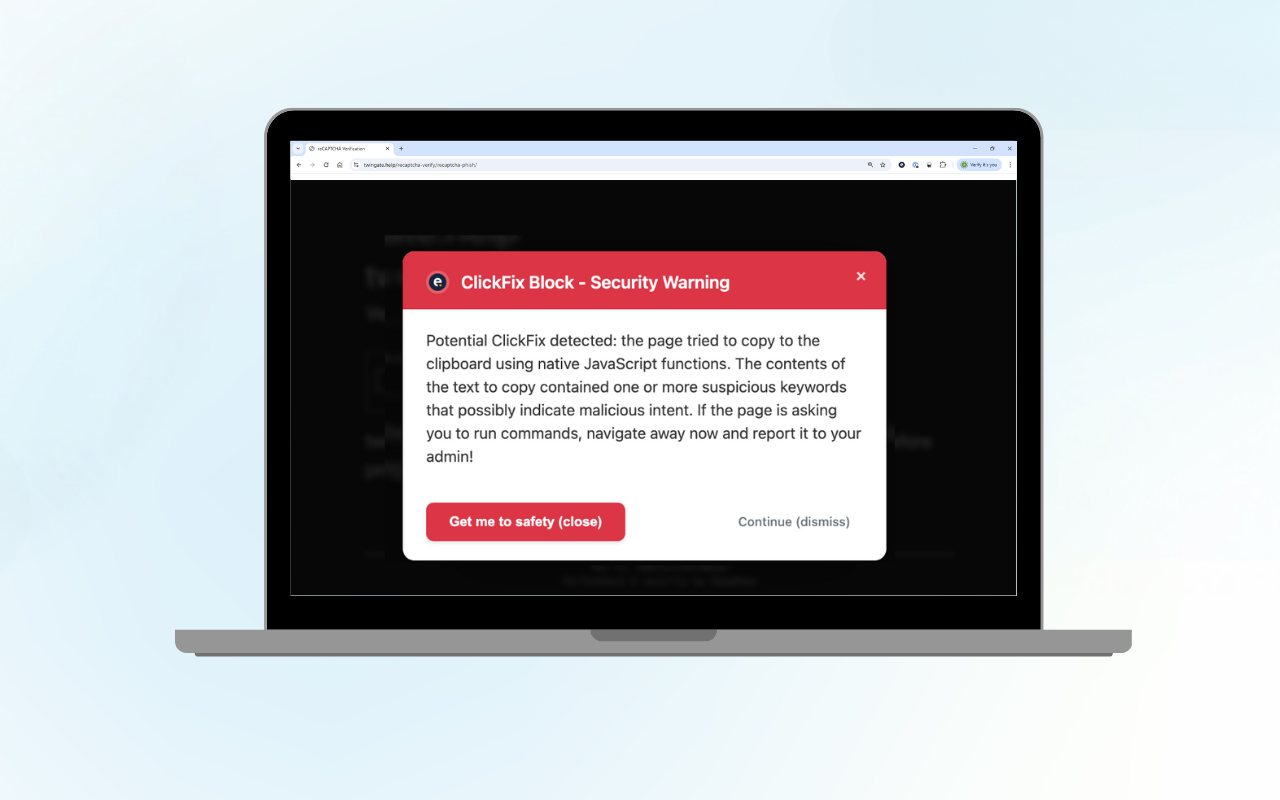
ClickFix Block: Protect Your Organisation from Fake CAPTCHA Attacks
Curious about the technical details? Read our technical blog on ClickFix Block....

Uses of AI in Enterprise Cybersecurity: Risks, Opportunities, Strategies
To fully unlock the potential of AI systems in cybersecurity, organisations...

Sneaky 2FA: Use This KQL Query to Stay Ahead of the Emerging Threat
At Eye Security, we constantly seek out new threats and detection methods to...

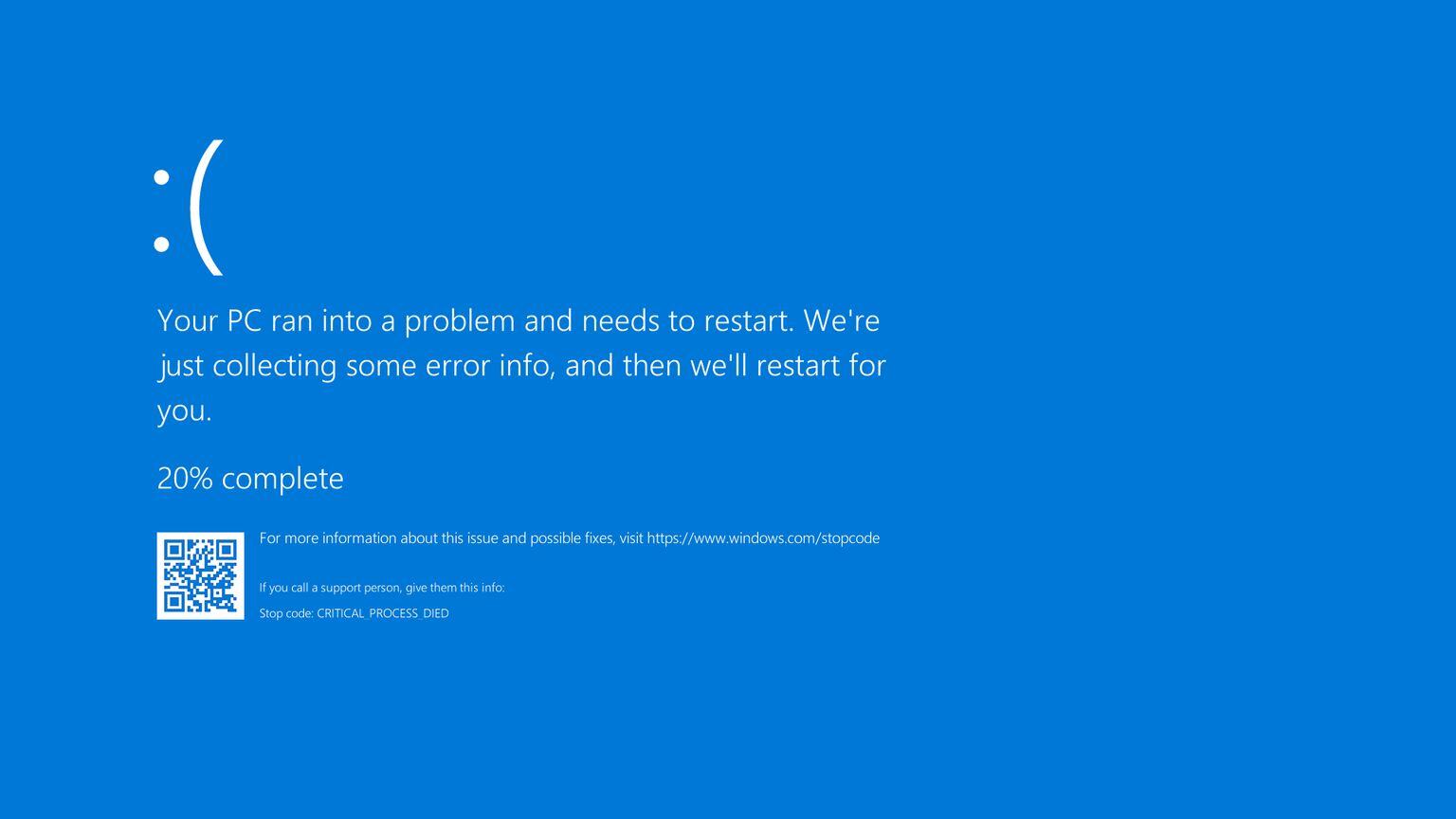
CrowdStrike Falcon and Microsoft blue screen issue updates
Last updated: July 30th at 00:00 CEST In this blog, we provided real-time...

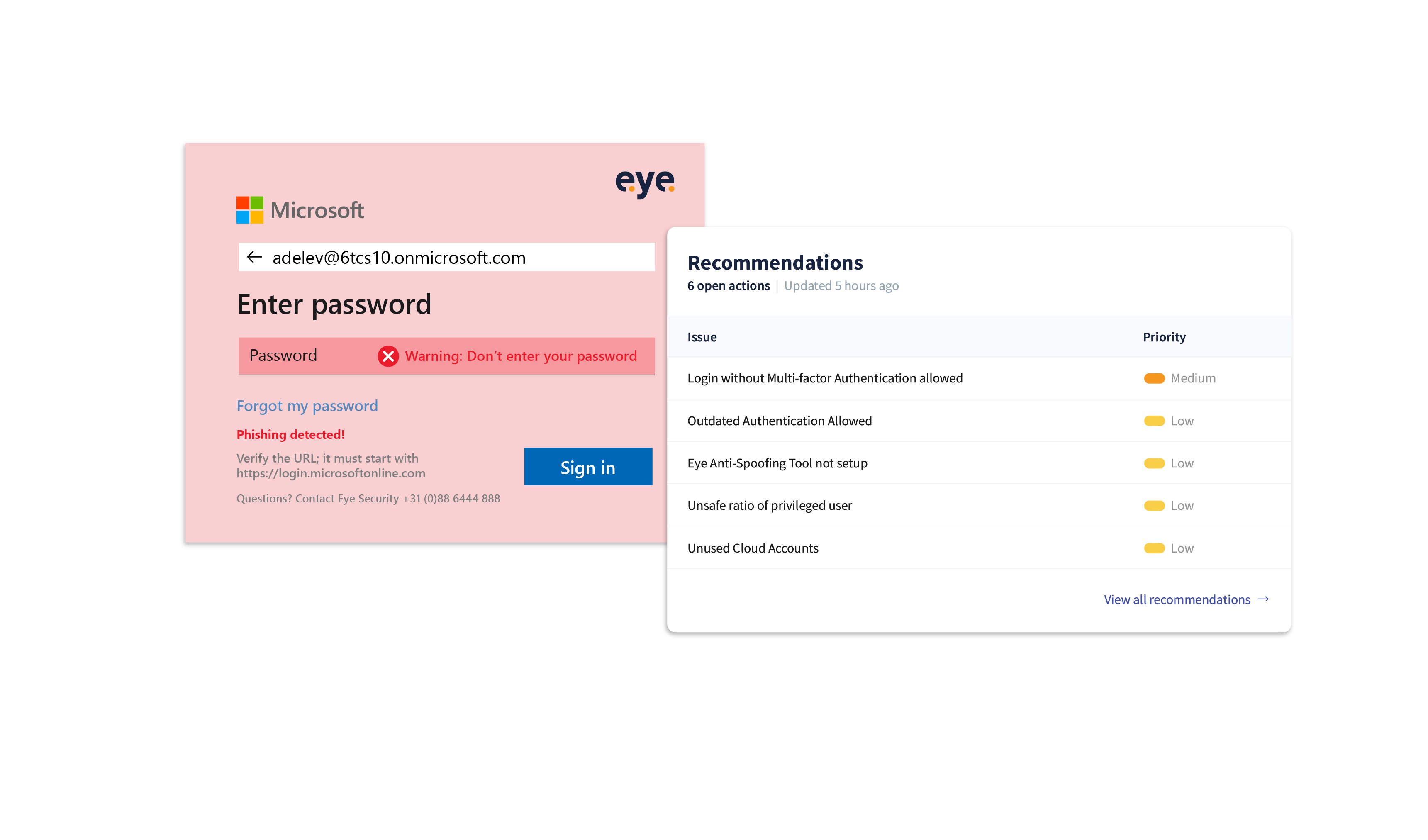
Empowering security: the battle against Login Spoofing
Introduction Battling cyber-crime can sometimes feel like an endless tennis...
A Conti-nuous issue
Introduction In this blog, we shed light on our findings during a forensic...

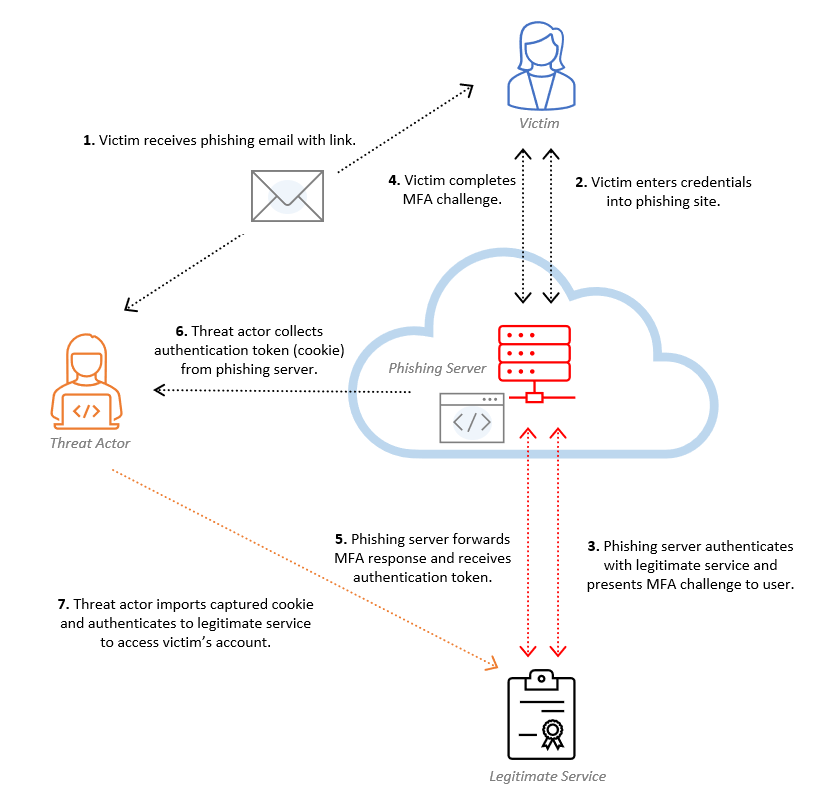
How to defend against EvilProxy when a phishing attack strikes
Here at Eye Security, we have observed a disturbing increase in security...

