Blogs.

Microsoft 365 AitM Phishing Protection: Free Browser Extension
Adversary-in-the-Middle (AitM) phishing is a rapidly growing threat that can...

The State of Incident Response 2026: Insights from 630 Investigations
Eye Security analysed 630 anonymised cybersecurity incidents across Europe...
From Helper To Risk Factor: Why AI Canvases Deserve Executive Attention
Eye Research demonstrated that a shared AI canvas can convincingly imitate...


AI Agents in Cybersecurity: What’s Real, What’s Hype, and What's Next
Artificial intelligence is everywhere in cybersecurity conversations right now....

The Cyber Threat Landscape 2026: Building Resilience, Acting Fast
Cyber defence is entering a race measured in minutes, not days. As we move into...

Microsoft 365 AitM Phishing Protection: Free Browser Extension
Adversary-in-the-Middle (AitM) phishing is a rapidly growing threat that can...
Insights from the SOC: Why Analysts Still Matter in the Age of AI
Every week, vendors announce new AI tools promising autonomous defence and...
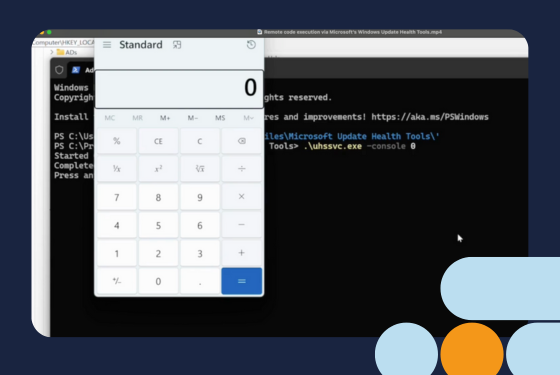
Remote code execution via Microsoft’s Windows Update Health Tools
For readers who want the full technical analysis, the detailed research blog is...

Battling Shadow AI: A Practical Tool for CISOs
Generative AI is transforming how businesses operate. Tools such as ChatGPT,...


Top Cyber Threats in Logistics and How to Defend Against Them
For decades, transport and logistics operators have focused primarily on...
When Business Email Compromise Nearly Costs a Million: An Incident Response Story
Business Email Compromise (BEC) remains one of the most damaging yet...

 Bas van den Berg
Bas van den Berg
