Blogs.

Microsoft 365 AitM Phishing Protection: Free Browser Extension
Adversary-in-the-Middle (AitM) phishing is a rapidly growing threat that can...

The State of Incident Response 2026: Insights from 630 Investigations
Eye Security analysed 630 anonymised cybersecurity incidents across Europe...
From Helper To Risk Factor: Why AI Canvases Deserve Executive Attention
Eye Research demonstrated that a shared AI canvas can convincingly imitate...


AI Agents in Cybersecurity: What’s Real, What’s Hype, and What's Next
Artificial intelligence is everywhere in cybersecurity conversations right now....

The Cyber Threat Landscape 2026: Building Resilience, Acting Fast
Cyber defence is entering a race measured in minutes, not days. As we move into...

Microsoft 365 AitM Phishing Protection: Free Browser Extension
Adversary-in-the-Middle (AitM) phishing is a rapidly growing threat that can...
Insights from the SOC: Why Analysts Still Matter in the Age of AI
Every week, vendors announce new AI tools promising autonomous defence and...
ClickFix Block: Protect Your Organisation from Fake CAPTCHA Attacks
Curious about the technical details? Read our technical blog on ClickFix Block....

A new paradigm to extinguish cyber risk for good: 24/7 protection connects with cyber insurance
...
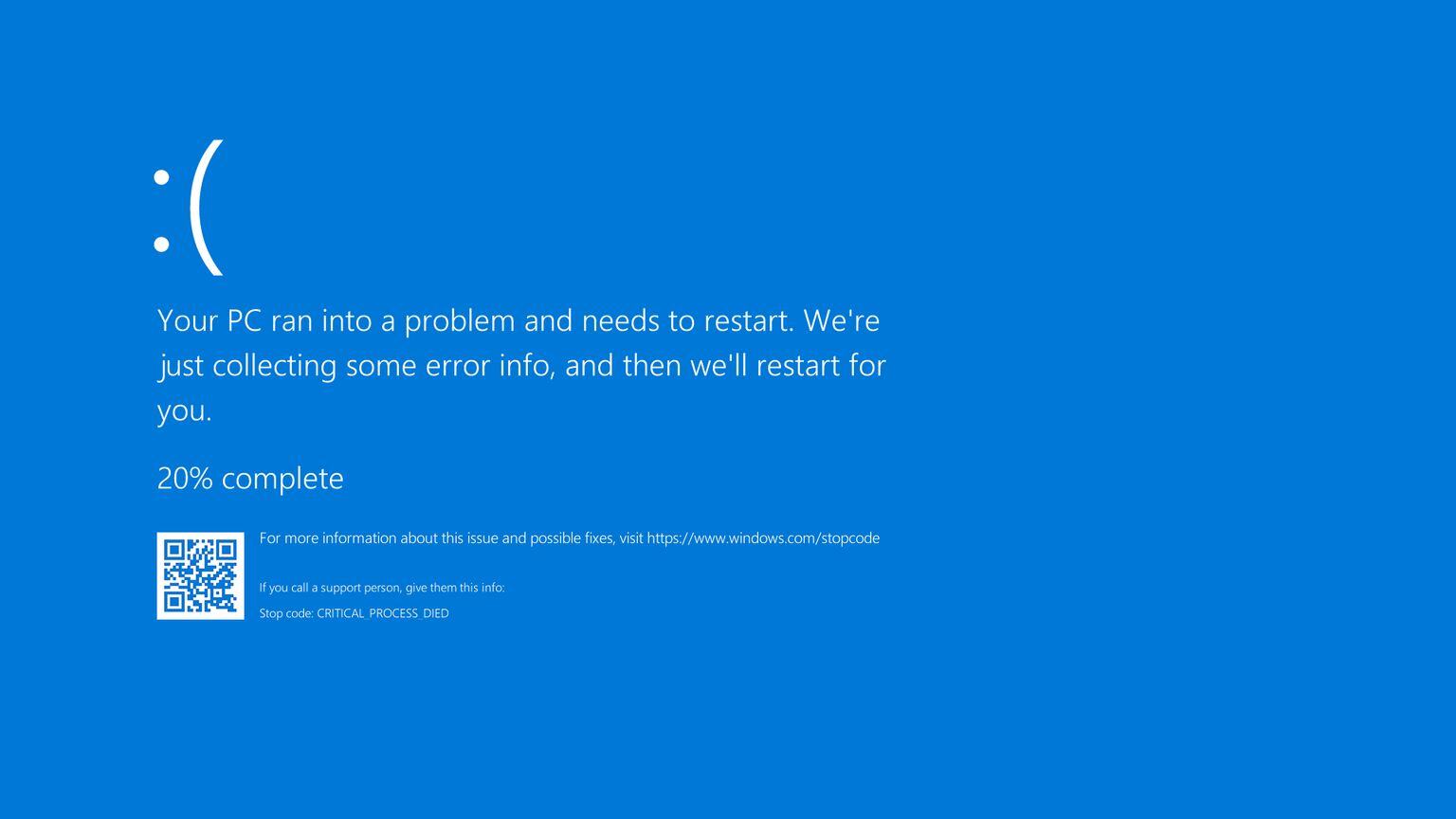
CrowdStrike Falcon and Microsoft blue screen issue updates
Last updated: July 30th at 00:00 CEST In this blog, we provided real-time...


NIS2 Directive Overview: In-depth look at Articles 21 and 23
While many EU countries are still working out the specifics of implementing the...

