Blogs.

Microsoft 365 AitM Phishing Protection: Free Browser Extension
Adversary-in-the-Middle (AitM) phishing is a rapidly growing threat that can...

Log poisoning in AI agents: The OpenClaw case
For the full technical analysis, please visit the Eye Research website. AI...


The State of Incident Response 2026: Insights from 630 Investigations
Eye Security analysed 630 anonymised cybersecurity incidents across Europe...

The Cyber Threat Landscape 2026: Building Resilience, Acting Fast
Cyber defence is entering a race measured in minutes, not days. As we move into...

Microsoft 365 AitM Phishing Protection: Free Browser Extension
Adversary-in-the-Middle (AitM) phishing is a rapidly growing threat that can...
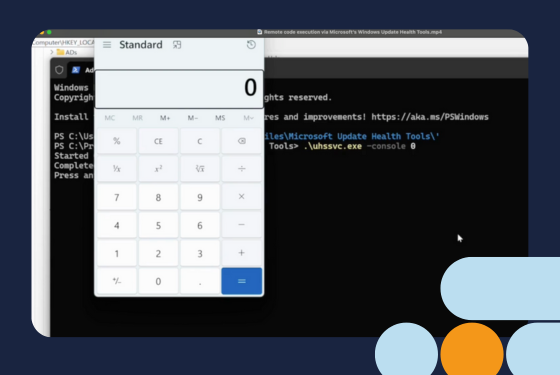
Remote code execution via Microsoft’s Windows Update Health Tools
For readers who want the full technical analysis, the detailed research blog is...
When Business Email Compromise Nearly Costs a Million: An Incident Response Story
Business Email Compromise (BEC) remains one of the most damaging yet...


Dual-use AI in Cyberattacks: How LLMs Are Reshaping the Threat Landscape
The malicious use of AI is evolving, making attacker tactics increasingly...

Hours from shutdown: How a Logistics company escaped ransomware just in time
This is a real incident Eye Security investigated at Move Intermodal. The...

Eye Security Uncovers Actively Exploited Zero-Day in Microsoft SharePoint (CVE-2025-53770)
On the evening of July 18, 2025, Eye Security identified active, large-scale...
Inside a Ransomware Attack: What a Real-World Incident Can Teach Us
“All systems went dark. We are locked out of everything. We don’t know how far...

 Bas van den Berg
Bas van den Berg
