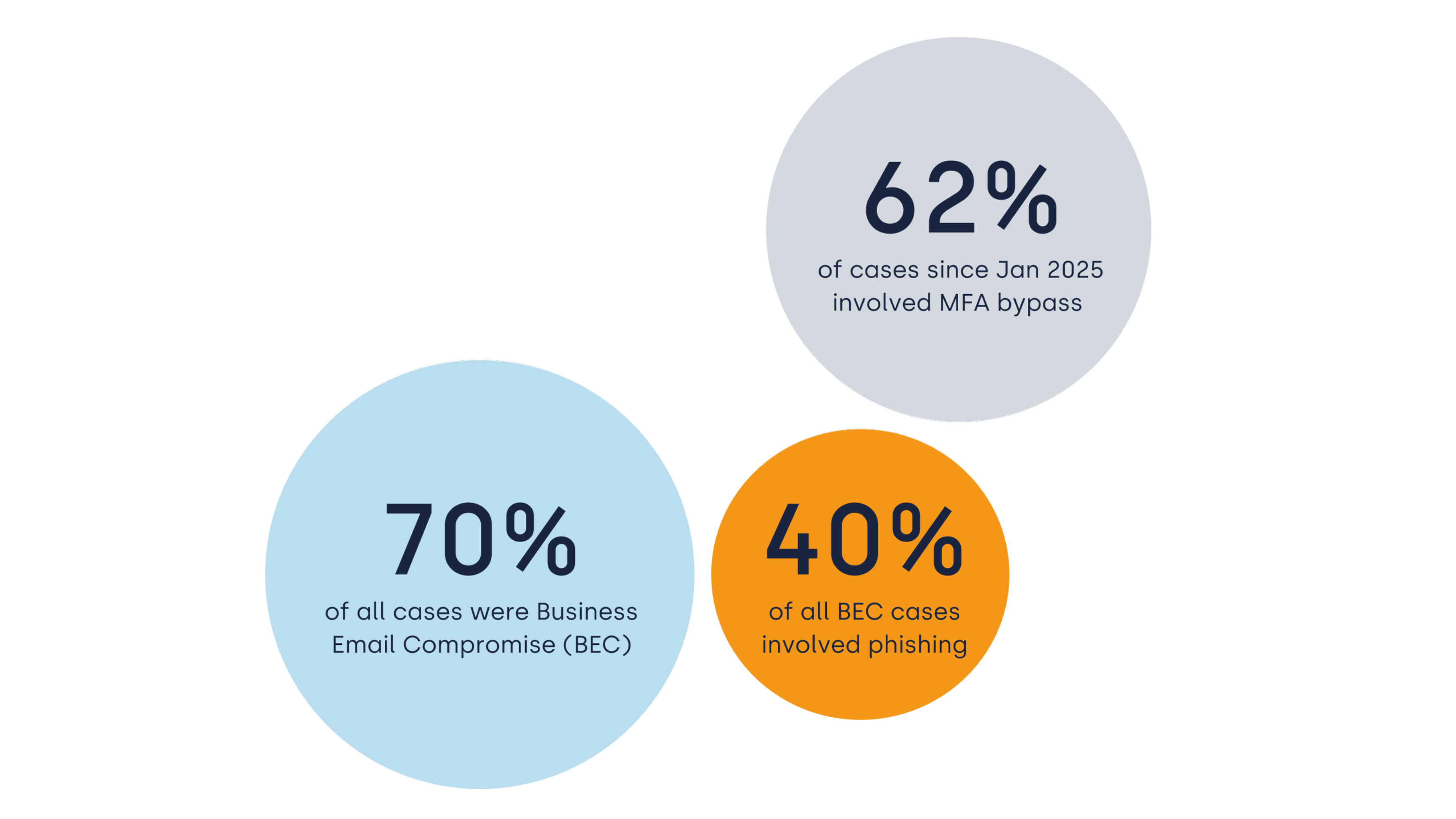
Business Email Compromise (BEC) remains one of the most damaging yet underestimated forms of cybercrime. Unlike ransomware, which makes headlines with dramatic lockouts and ransom notes, BEC thrives on subtlety, deception, and the exploitation of trust. In our latest Incident Response webinar, we walk through a real case in which attackers infiltrated email accounts and orchestrated fraudulent transactions that nearly cost an international organisation a million.
This article unpacks the chronology of the attack, the investigation process, and the lessons learned with insights for IT and finance leaders.
Day 1. A missing payment
It all started with a phone call. A finance controller at a national branch of an international membership organisation reported that a large international payment had not arrived. What initially appeared to be a routine delay quickly unraveled into a far more serious challenge.
The attackers had manipulated legitimate invoices and inserted new bank account details. Money was being transferred but not to the intended recipients.
Day 2. Mapping the damage
As the finance team retraced the payment trail, the scale of the fraud came into focus. Multiple international payments, together worth close to a million, were missing.
The pattern suggested a compromise of email communication between the finance controllers of the international headquarters and the national organisations. Emails requesting payment, complete with genuine invoices, had been followed up by emails containing fraudulent bank account details.
At this point, Eye Security’s Incident Response (IR) team was called in.
 Image 1. The mechanics of the attack: real invoices sent out by the genuine email account owner were followed up by emails with "updated" fake bank details, sent out by the threat actor
Image 1. The mechanics of the attack: real invoices sent out by the genuine email account owner were followed up by emails with "updated" fake bank details, sent out by the threat actor
Day 3. The forensic investigation begins
The first step was to determine whether the organisation’s email servers had been compromised. The investigation quickly confirmed they had not. Instead, the attackers had gained direct access to the mailbox of the international finance controller.
This pointed to stolen credentials rather than an infrastructure breach. The question was: how had the attackers obtained them?
Day 4. Root cause identified
By analysing browser histories and email records, investigators traced the intrusion back to a phishing campaign. An email had been sent to multiple staff members three months earlier. One employee had clicked on a link and entered login credentials into a convincing phishing page.
The attackers had used this information to access the account, bypassing multi-factor authentication.
From that moment on, the attackers had full visibility into the finance controller’s communications.
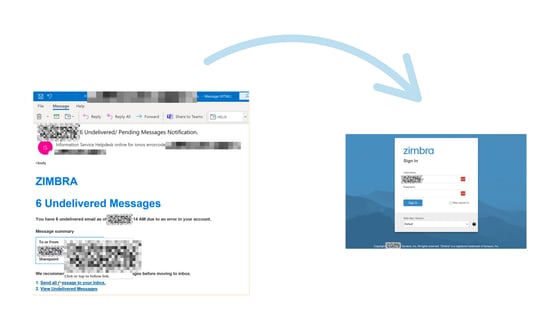
Image 2. The attack began when a finance controller received what appeared to be a standard email with a link. The phishing message was branded like a legitimate service but led to a credential-harvesting page. When the link was opened, the page perfectly imitated a trusted login portal. Credentials entered here gave attackers a direct line into the mailbox.
Business email compromise: how the fraud worked
The attackers monitored email traffic for weeks, studying processes, approvals, and supplier onboarding steps. The first fraudulent email was sent seven weeks before the compromise was discovered. By then, multiple payments had already been redirected.
This is how it worked: When a legitimate invoice was sent by the genuine email account owner (who was entirely unaware of the threat actors controlling the account), the attackers followed up with a fraudulent email containing "updated" bank details. To the local finance teams, the message appeared entirely authentic.
The attackers went further, exploiting the organisation's supplier onboarding process. Upon receiving the email with fake bank details, the financial controller of the national organisation did pay the invoice but additionally pointed to the correct process of providing these, via a new supplier form.
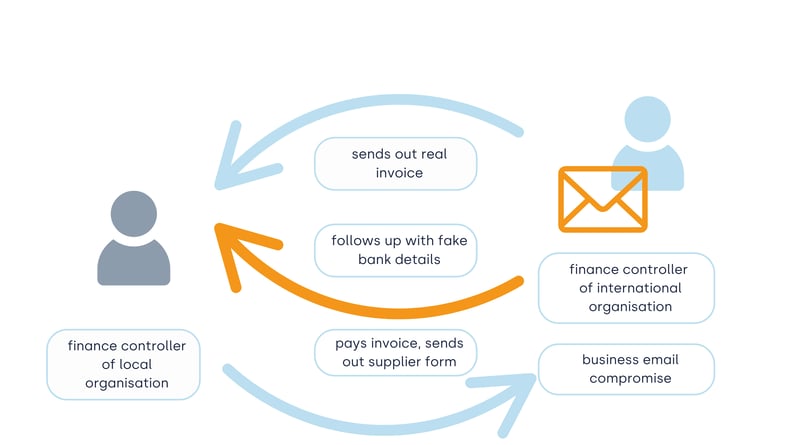
Image 3. Threat actors learn about the correct process involving a "new supplier form" and use it to insert themselves into real workflows
Once the threat actors learned how new bank accounts were approved within this organisation, they incorporated them into their process. This illustrates how attackers insert themselves into existing workflows, rather than creating fake ones from scratch.
Day 23. First lateral movement attempts
At this point, however, the attackers controlled just one email account, that of the international financial controller. To amplify the damage, the threat actor attempted to additionally take over further email accounts. Posing as the original email account owner, the attackers sent out phishing emails to other employees within the organisation.
We could identify two lateral movement attempts, both of which were unsuccessful.
Day 44. Payments start flowing in
The treat actors already had an established process, which they applied to several local organisations. The moment the email account holder, the actual finance controller of the international organisation, sent out an invoice, the attackers followed up with a fraudulent email sharing "updated" bank details via the new supplier form.
This is how the threat actors succeeded in appropriating funds totaling €1m, coming from several local organisations.
 Image 4. Adopting the established process, the threat actors redirect multiple payments to fraudulent bank accounts
Image 4. Adopting the established process, the threat actors redirect multiple payments to fraudulent bank accounts
The attack timeline at a glance
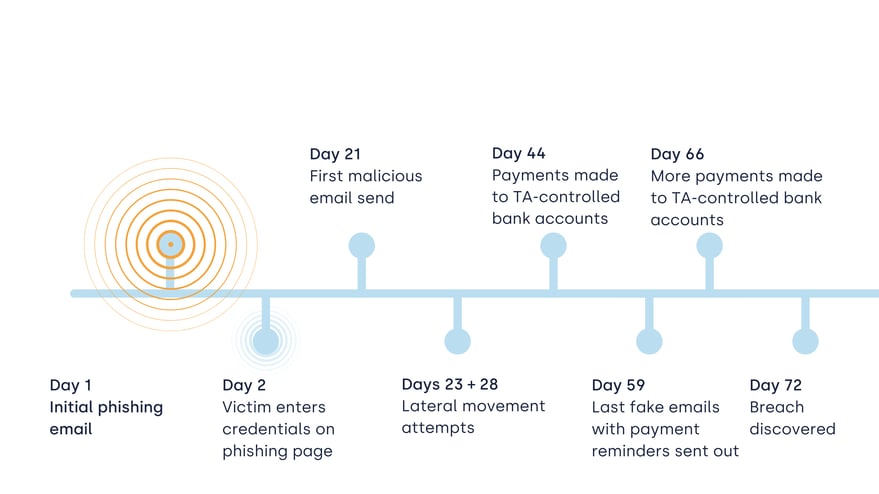
Image 5. Attack timeline from the initial phishing email to the discovery of the breach 72 days later
- Day 1 – First phishing email delivered.
- Day 2 – Victim enters credentials on phishing site.
- Day 21 – First fraudulent email sent, citing new bank details.
- Day 23 + 28 – Attempts at lateral movement into other accounts.
- Day 44 – Payments start flowing into attacker-controlled bank accounts.
- Day 59 – Last fraudulent payment reminders sent.
- Day 66 – More payments transferred to attacker accounts.
- Day 72 – Incident discovered, IR engaged.
The timeline graphic lays bare the scale of the compromise, from the very first phishing email to the discovery more than 70 days later. Each marker, first malicious login, first fraudulent email, lateral movement attempts, tells the story of attackers remaining undetected for weeks. The takeaway: without continuous monitoring, weeks of undiscovered fraudulent activity can translate into massive financial losses.
See the full forensic walkthrough and expert discussion in our on-demand webinar.
In this case, the direct fraud amounted to roughly a million in missing payments. But the financial impact does not stop there. Typically, organisation also face:
The true cost of a BEC attack, however, extends far beyond the stolen funds. It affects client trust, staff workload, and even the long-term resilience of the organisation.
Moving to cloud-based email systems offers advantages in resilience and security. But cloud monitoring often falls outside of traditional security scopes. Without 24/7 monitoring, suspicious logins and mailbox rule changes may go unnoticed for weeks.
The phishing page used in this attack bypassed MFA. While MFA remains essential, it must be complemented with continuous monitoring and detection to spot unusual behaviour.
The fraud exploited weaknesses in payment approval processes. Implementing the four-eyes principle (dual approval for bank detail changes) could have blocked fraudulent payments, even if email compromise occurred.
Had Managed Detection & Response (MDR) been in place, the story might have unfolded very differently.
With MDR, the compromise would likely have been neutralised within 10 minutes, preventing financial losses from the outset.
Business Email Compromise incidents demonstrate that prevention alone is not enough. Organisations must assume breach and be ready to detect and respond quickly. Eye Security supports MSPs and their clients with a complete approach to cyber resilience:
This BEC incident highlights that trust is the attacker’s greatest weapon. By carefully imitating legitimate communications, cybercriminals bypass technical defences and exploit human processes.
Business Email Compromise is not going away. But with the right defences, monitoring, and processes, organisations can transform into resilient defenders.