A surge of high-impact cyberattacks is shaking the retail sector, exposing vulnerabilities even among digitally mature giants like Marks & Spencer, Harrods, Victoria’s Secret, and UNFI. These incidents, ranging from ransomware to widespread supply chain disruption, expose a sobering truth: no organisation is immune, regardless of brand strength or investment in cybersecurity.
In just a matter of weeks, UK's Marks & Spencer and grocery chain Co-op, luxury retailer Harrods, clothing brand The North Face and luxury jeweller Cartier, Victoria’s Secret, and, most recently, United Natural Foods Inc., have confirmed cyber incidents ranging from ransomware deployment to unauthorised access and data exfiltration. And let us emphasise: here we talk about high-profile, digitally mature organisations with high-stakes digital environments and robust protection in place. Each case vividly demonstrates that even well-resourced companies with strong brand reputations are vulnerable. Whether these incidents are connected or opportunistic, the world of retail is being tested at scale.
- M&S suffered one of the most damaging ransomware attacks in UK retail history, with stolen credentials, encrypted servers, and an estimated £500M+ market value drop in days.
- Harrods responded swiftly to an attempted breach by restricting network access but the investigation continues. Financial damage is still unfolding.
- Victoria’s Secret had its e-commerce operations offline over a peak shopping weekend. Lingering corporate IT outages and reputational impact were reflected in its falling share price.
The EU's NIS2 Directive now places heightened obligations on retailers, including mandatory breach detection, vendor oversight, and executive accountability. This shift reflects a broader security imperative: assume breach and act.
Know how you would respond.
Get the cyber incident readiness checklist.
At Eye Security, we have not observed any direct impact within our customer base. However, with multiple retail clients in our portfolio, we urge all businesses: do not wait for signs of compromise. Harden access, invest in 24/7 detection and response. The attackers may already be here.
It all started with a shock: Marks & Spencer (M&S)
Marks & Spencer was the first in a line of cyber incidents with major retailers. BBC News reports that the hacking group Scattered Spider, composed of English-speaking teens and young adults, is the prime suspect. They used a malicious cybercrime service called DragonForce, which offers ransomware tools to paying affiliates.
According to the press, DragonForce sent out an email to CEO Stuart Machin to boast about the attack and demand payment. The email appears to have been sent from the account of an employee at Tata Consultancy Services, an IT partner.
According to Machin, the threat actors infiltrated M&S systems via social engineering. Essentially, they posed as trusted individuals to gain access through a third-party provider. The UK’s National Cyber Security Centre warns that this impersonation tactic is becoming a common method to breach British retailers.
Attack timeline and key events:
- February – March 2025: Initial breach occurrs through third-party vendor (TCS), using social engineering such as help-desk impersonation and SIM swapping
- April 21–22: Attackers deploy DragonForce ransomware across the network, encrypting VMware ESXi servers; M&S detected the breach during Easter weekend
- Apr 22: M&S discloses the cyber incident publicly via filing
- Apr 25: Online clothing, home orders, contactless payments, and Click & Collect services suspended
- May 13: M&S confirms unauthorised access to sensitive data
- May 19: Company projects impact into July; cost estimates at £60 m–£300 m in lost profit and over £1 bn in market capitalisation
- Jun 10: Online ordering restored after six weeks offline
Harrods confirms cyber attack and launches forensic investigations
In early May, the luxury retailer Harrods confirmed attempts to breach its systems, prompting the company to restrict internet access at its sites, though its stores and website remain operational.
Customer-facing operations remained active but the company restricted internet access across its sites as a precaution, signaling a potentially serious underlying threat.
No official financial losses have been disclosed. At the same time, the stakes are high. Harrods handles large volumes of high-net-worth customer data, making it an attractive target for extortion. Even short-term disruptions or perceived vulnerabilities can carry steep reputational costs, particularly in the luxury retail segment that is heavily reliant on brand trust.
As of now, Harrods is advising customers that no action is required. Forensic investigations are ongoing.
Attack timeline and key events:
- May 1, 2025: Harrods first detects an unauthorised access attempt to its systems and responds by restricting internet access across sites
- Actions: Takes proactive measures to isolate systems; physical stores and e-commerce remain operational
- NCSC confirms coordination with Harrods and other retailers
- No confirmation of ransomware or data encryption
- Speculations of whether the attack is likely part of a wider campaign targeting retailers, particularly through third-party or supply-chain vectors.
Victoria's Secret cyberattack: critical systems now restored
Between May 24 and May 26, 2025, Victoria’s Secret was wrestling with a major cyberattack that shut down its e-commerce platform and corporate systems. The disruption affected some in-store services and prompted the company to activate emergency protocols. In a subsequent SEC filing, the retailer confirmed that all critical systems are now restored and fully operational, with external cybersecurity experts engaged to investigate the breach.
Despite the disruption, the company stated that the incident is not expected to materially impact fiscal 2025 results, though some remediation costs will still be incurred. However, the cyberattack delayed the release of its Q1 earnings, initially scheduled after May 3, 2025. Systems required to finalise financial reporting were inaccessible during the recovery window.
Victoria’s Secret, which operates over 1,380 stores in nearly 70 countries and reported $1.353 billion in Q1 sales, has not confirmed whether ransomware was involved. No cybercrime group has claimed responsibility.
Attack timeline and key events:
- May 25–26, 2025: A security incident disrupted operations during the local Memorial Day holiday, likely timed to take advantage of staff shortages
- May 26: Corporate systems and e-commerce site taken offline; response protocols initiated
- May 28: Website remained down; some in-store services disabled; physical stores remained open
- May 29: Website restored and operations resumed
- No public attribution yet
- Financial impact reported as minor in Q1 but undefined in Q2 due to extra cleanup costs.
The latest cyberattack in retail: United Natural Foods Inc. (UNFI)
When cybercriminals hit United Natural Foods Inc. (UNFI), one of the largest organic food distributors in the U.S., the ripple effects were immediate and visible. Whole Foods shelves across the country went bare. The June 5 ransomware attack forced UNFI to take critical systems offline, disrupting communication with stores and halting accurate deliveries. This resulted in bread shortages, empty produce bins, and shutdowns of in-store services.
Employees at multiple Whole Foods locations reported chaos behind the scenes. There were accounts of wrong shipments, overstocked goods no one asked for, and basic supplies like trash bags running low. The takeaway: with complex supply chains involving dozens of interconnected companies, a single compromised vendor can paralyse distribution nationwide.
UNFI saw its stock plunge 17.3%, erasing approximately $292 million in market value within two days following the June 5 cyber incident. Shares dropped over 8% on the initial disclosure and faced continued pressure as supply disruptions lingered. The company also revised its earnings guidance.
Attack timeline and key events:
- Jun 5, 2025: Unauthorised activity detected on internal networks; proactive shutdown of affected systems initiated
- Jun 9: UNFI formally filed with SEC, confirming system outages and ongoing forensic investigation with law enforcement
- Jun 10–11: Whole Foods warned of nationwide product shortages; UNFI began phased system restoration
- Jun 11–12: Market reaction drove stock down 17%; investigations and recovery efforts continued
- Supply chain impact was immediate with orders disrupted and shelves emptied.
- UNFI’s scale (supplying 30 k+ stores) magnifies its industry vulnerability.
Summary of the major retail cyberattacks and anticipated financial impact in 2025
|
Retailer |
Attack date(s) |
Nature of attack |
Estimated financial impact |
Notable disruptions |
|
Marks & Spencer (M&S) |
Feb–Apr 2025 (detected Apr 21) |
Ransomware via DragonForce |
£60M–£300M lost profit; >£1B market cap drop |
Online ordering, Click & Collect, payments disabled; customer data breached |
|
Harrods |
May 1, 2025 |
Unauthorised access attempt |
Not disclosed publicly |
Internet restricted; no service outage; possible threat via shared supply chain |
|
Victoria’s Secret |
May 25–26, 2025 |
Undisclosed |
Not disclosed publicly |
E-commerce and internal systems offline over Memorial Day; recovery took ~4 days |
|
United Natural Foods (UNFI) |
June 5, 2025 |
Undisclosed, suspected ransomware |
market value drop; revenue disruption |
Whole Foods shelves empty; disrupted logistics across U.S. due to system shutdowns |
- M&S: Attack confirmed to have entered via TCS (a third-party IT vendor). Operations were down for over 6 weeks. Analysts estimate millions lost daily in sales alone.
- Harrods: Impact was limited due to quick isolation of networks. Full scope remains unclear.
- Victoria’s Secret: Though the company minimised the communication, experts estimate moderate disruption cost due to timing.
- UNFI: One of the most widespread supply chain impacts. Effects visible in Whole Foods across the U.S.
Why is retail so highly targeted?
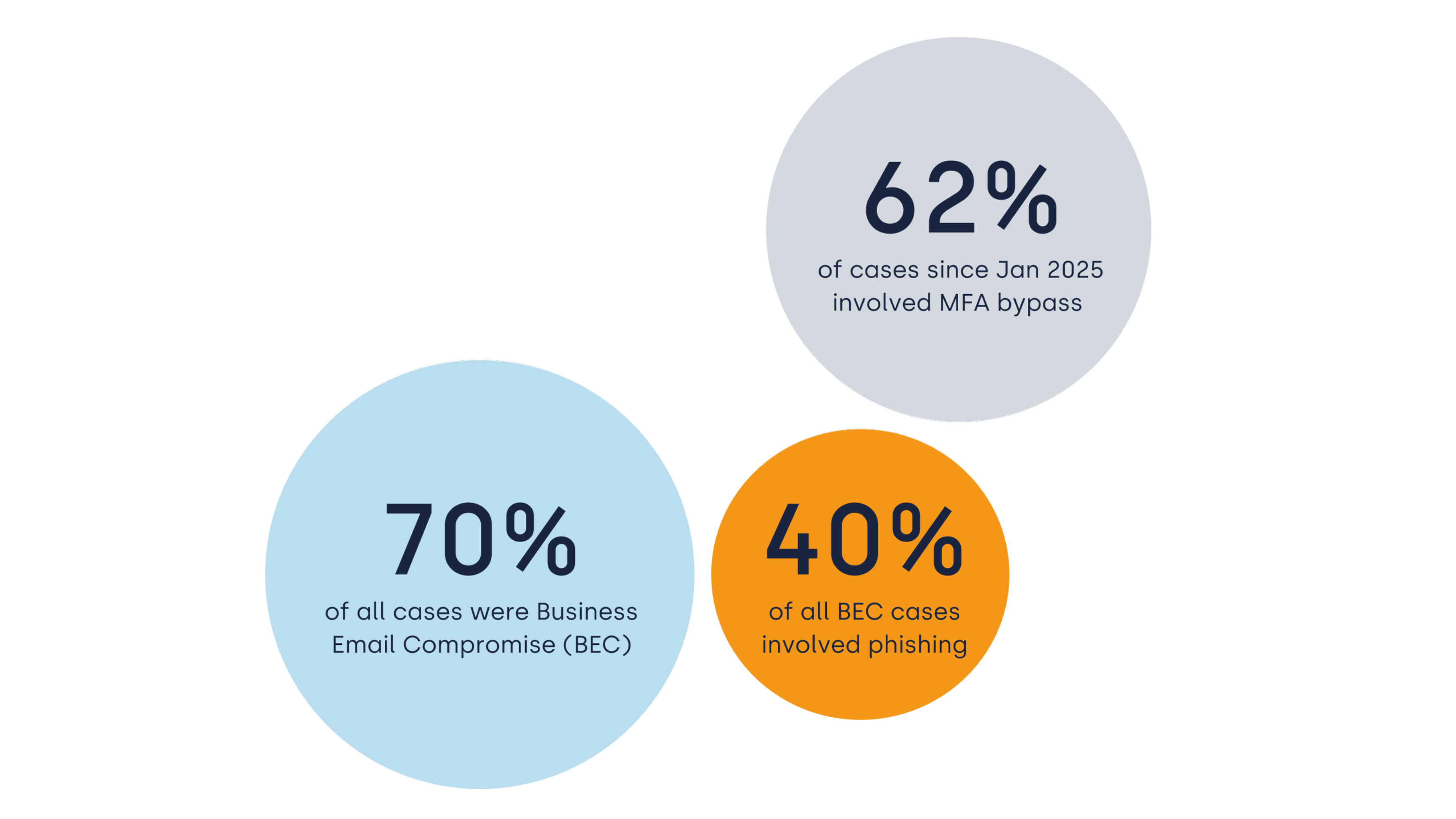
Retail ranks among the top five industries most vulnerable to cyberattacks. Attackers are after high-value personal data, ecommerce cash flows, and access to retail infrastructure. For businesses, the cost of inaction can be catastrophic: lost revenue, shattered trust, regulatory penalties, and even bankruptcy.
25% of global attacks now target retail, where the average data breach costs $4.88 million. In fact, nearly half of retail web traffic is bots, tools for scraping data, launching DDoS attacks, and cracking stolen credentials.
And 43% of attacks target small businesses, with over 60% closing shop within six months of a breach.
Among the most dangerous threats for retail are:
- Phishing, responsible for 43% of attacks
- Ransomware, affecting 69% of retail companies, whereby only 26% stopped the encryption
- DDoS attacks, fueled by malicious botnets, now account for 40% of traffic to retail sites
- Ecommerce fraud, costing $48 billion in 2023, slashing 2.9% of revenue
Even a single lapse can open the floodgates. What is it that companies can do right now?
- Encrypt everything
- Train your staff, knowing that 68% of breaches involve human error
- Vet vendors, patch vulnerabilities, and implement zero-trust security models
- Leverage AI-driven fraud detection
- Harden your web applications and protect your POS systems
- Do not wait to be attacked but invest in post-breach readiness now
Research shows that 82% of consumers will abandon a brand after a data breach.
Assume breach: why 24/7 protection becomes a must
At Eye Security, our experience responding to hundreds of incidents confirms what the data already shows. Cybercriminals thrive in silence. They often dwell in systems for days, weeks, or even months before launching the final, destructive phase of an attack.
This is why businesses must shift from prevention-only strategies to a proactive, “assume breach” mindset. Here are our top recommendations:
Invest in 24/7 monitoring and detection
Attackers do not clock out at 5pm. Modern cyberattacks are multi-stage, often beginning with initial access through phishing or unpatched vulnerabilities, followed by lateral movement, credential theft, and data exfiltration. Without round-the-clock detection, these activities can go unnoticed.
24/7 Security Operations Center (SOC) coverage, powered by expert SOC analysts and AI-assisted threat detection, drastically reduces dwell time. Without it, the average breach goes undetected for an average of 204 days. A SOC can help you contain threats before data is stolen or encrypted.
Perform regular attack surface scans
Your attack surface, that is, the sum of all the ways a system can be accessed, is dynamic. New vulnerabilities emerge daily. Shadow IT, forgotten endpoints, and exposed services like misconfigured cloud storage or test environments create perfect entry points.
Frequent, automated scanning identifies and prioritises vulnerabilities before attackers do. Eye Security’s continuous scanning approach ensures businesses stay one step ahead, plugging gaps before they become entry points for ransomware or data theft.
Harden access points: you may already be compromised
Backdoors, compromised credentials, or dormant malware may already exist within your systems. We recommend that you introduce zero-trust principles. Further, we encourage you to limit administrative privileges and enforce MFA everywhere. Networks should be segmented to prevent lateral movement. Also, you may want to monitor for anomalous behavior tied to insider threats or compromised accounts. The assume breach principle dictates: assume that at least one layer of your defence has already failed.
To all European retailers: this is why NIS2 matters now
The recent surge in cyberattacks against retail giants is a regulatory flashpoint. In Europe, the NIS2 Directive is entering into force. And for the retail sector, too, compliance becomes strategic risk management.
NIS2 broadens the scope of cybersecurity regulation across the EU. Unlike its predecessor, it no longer applies solely to traditional critical infrastructure like energy or transport. Instead, it now explicitly includes key supply chain sectors, such as food distribution, e-commerce platforms, and major retailers, that is, exactly the types of businesses currently being targeted.
The directive mandates that these organisations implement strict cyber risk management, incident detection and reporting processes, and demonstrate resilience across their entire digital infrastructure, including third-party vendors.
NIS2 enforces a shift in mindset. It assumes breach. It demands that leadership be accountable for cybersecurity governance. It forces companies to assess not only their own defences, but also the resilience of their entire digital ecosystem, including suppliers, software providers, and service partners.
For EU retailers, NIS2 compliance is a demonstration of maturity, trustworthiness, and business continuity.
For details, visit the NIS2 resource hub.
In sum, do not wait for retail to be a warning sign
Cybercriminals are opportunistic. If a tactic works in one industry, it will be repurposed and redeployed across others in days. This is why readiness is your best defence. Assume breach, enable real-time visibility, and act proactively.