Blogs.
Retail Giants Breached: What the M&S, Harrods & UNFI Attacks Mean for Your Cyber Defences
A surge of high-impact cyberattacks is shaking the retail sector, exposing...

Sneaky 2FA: Use This KQL Query to Stay Ahead of the Emerging Threat
At Eye Security, we constantly seek out new threats and detection methods to...

Business Email Compromise: Fifteen Steps to Reduce the Risk
Business email compromise (BEC) is a concept that first appeared around 2013...

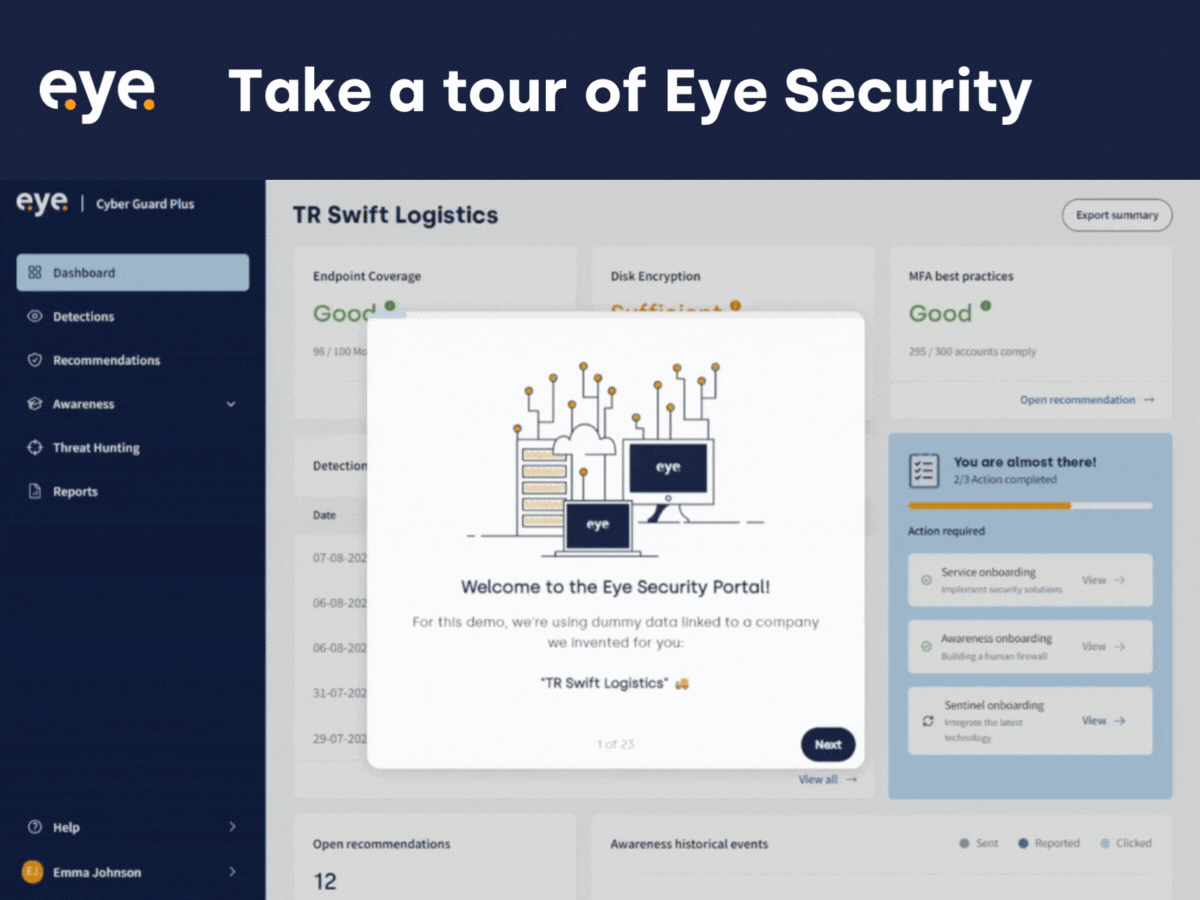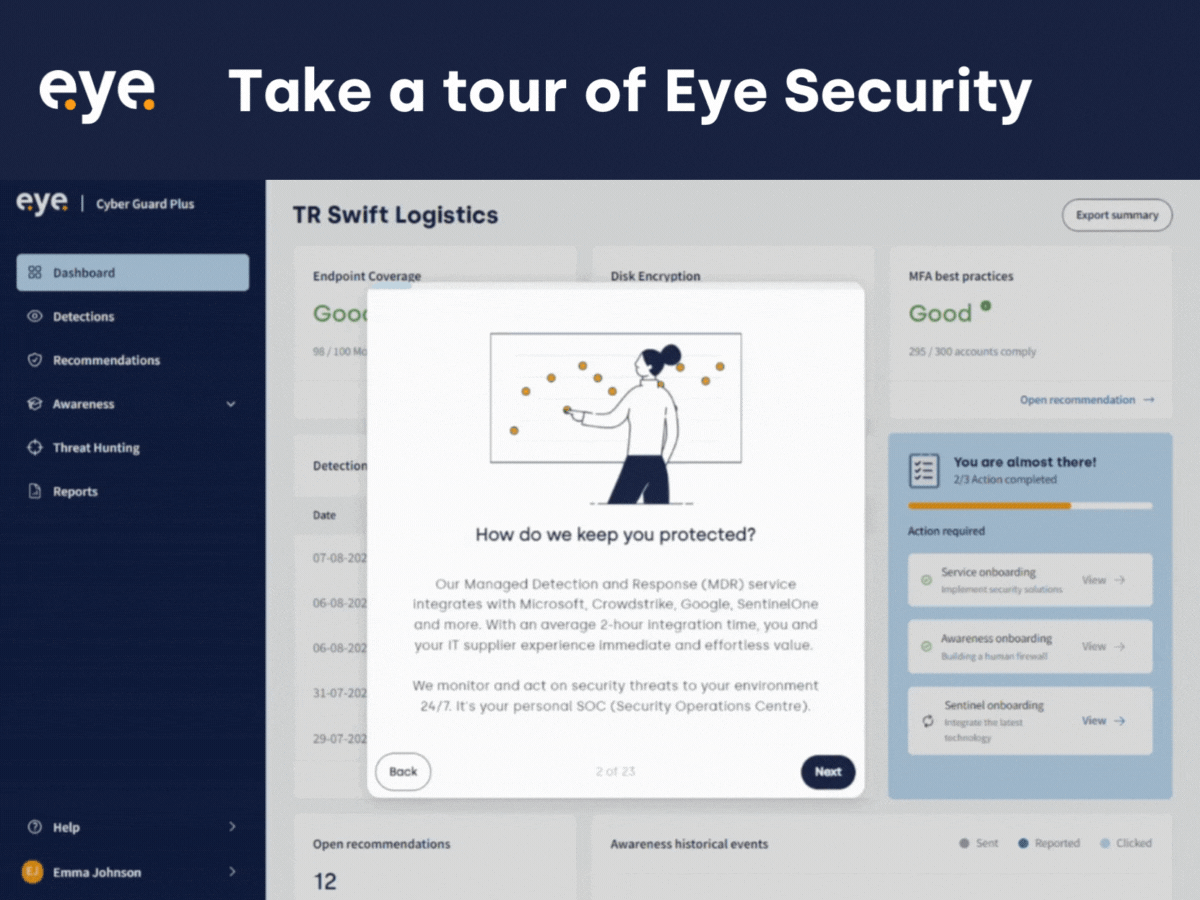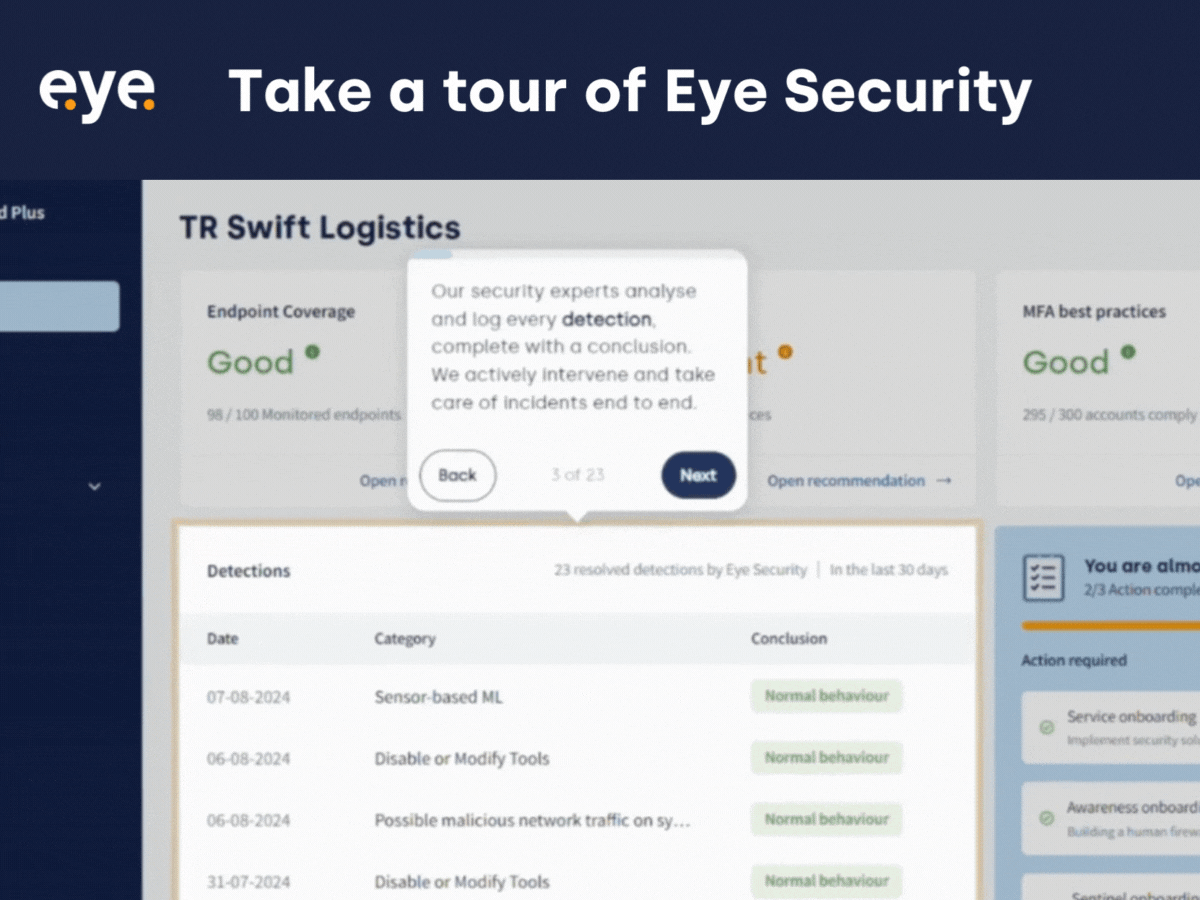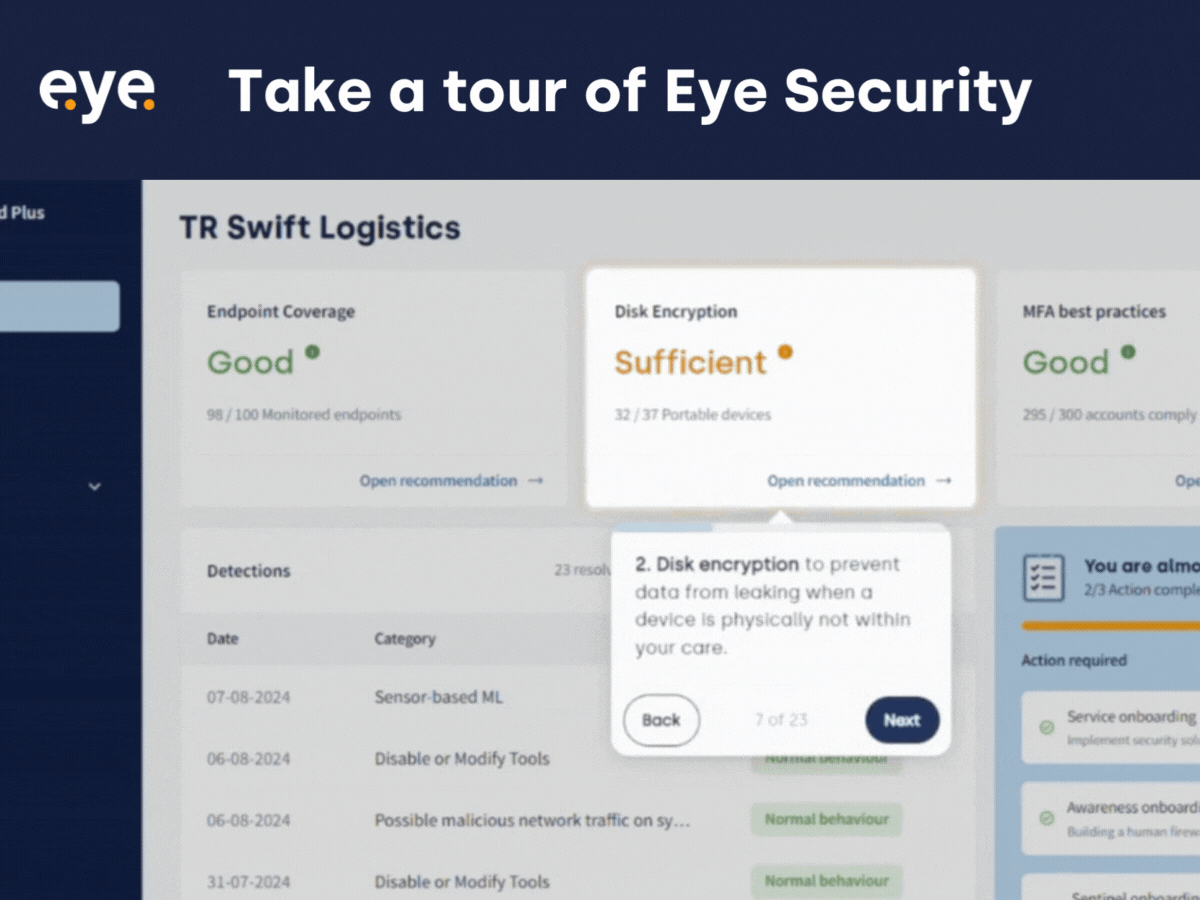
Product Update: Demo Portal
In this blog, we sit down with Anne Postma, our Product Manager, to discuss the...

Product Update: Vulnerability & Threat Hunting
In this blog, we interview Robbin Begeer, Product Manager at Eye Security,...
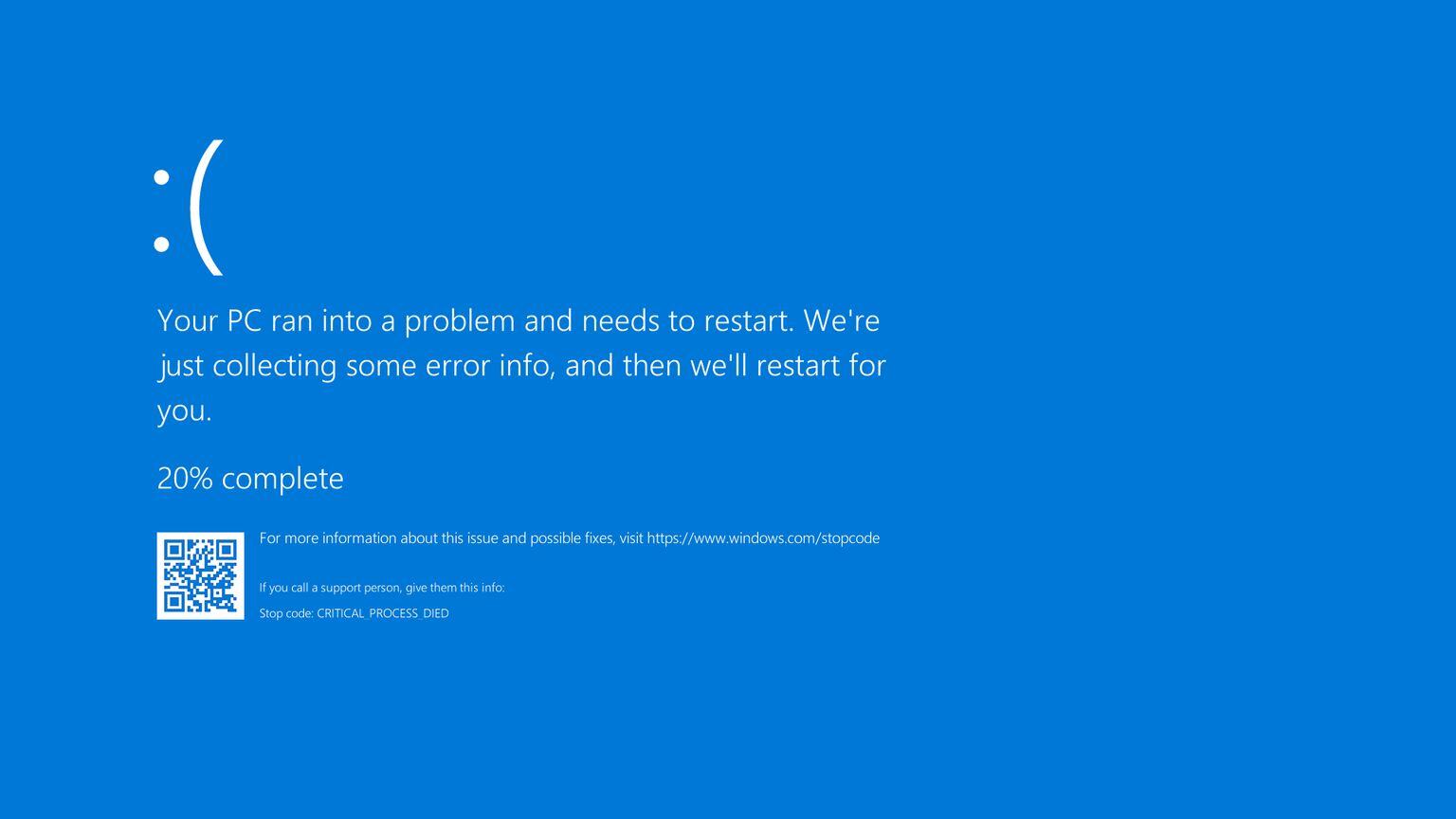
CrowdStrike Falcon and Microsoft blue screen issue updates
Last updated: July 30th at 00:00 CEST In this blog, we provided real-time...

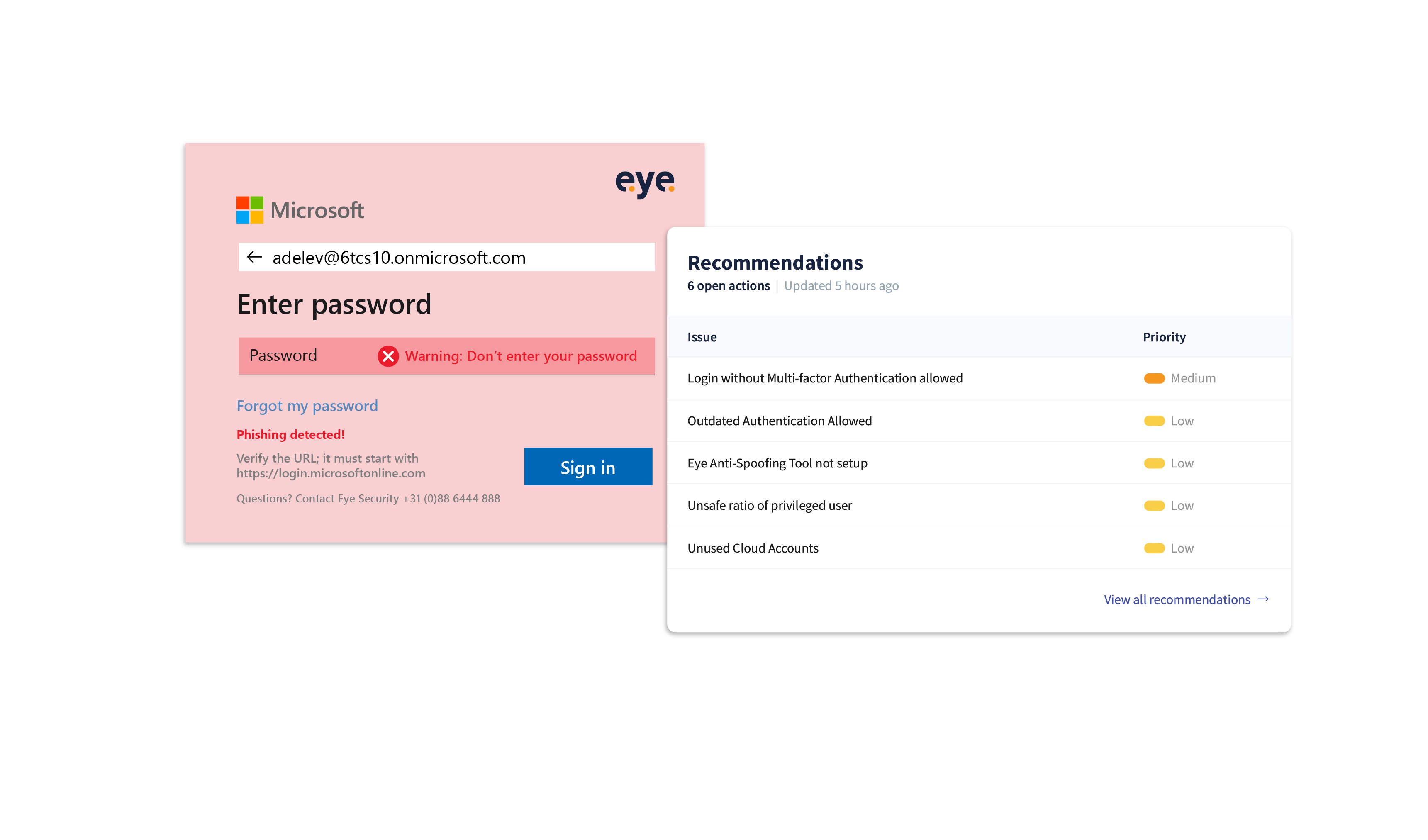
Empowering security: the battle against Login Spoofing
Introduction Battling cyber-crime can sometimes feel like an endless tennis...
A Conti-nuous issue
Introduction In this blog, we shed light on our findings during a forensic...


A case of ransomware, resolved
...

How we discovered outdated Windows Servers
Introduction Managing servers is the process of taking care of computer systems...
