Introduction
Around mid-September, our Security Operations Centre (SOC) received a high number of alerts via two of the Endpoint Detection and Response (EDR) solutions we monitor within our Managed Detection and Response (MDR) service, CrowdStrike and Defender forEndpoint. Initial analysis showed malware was being distributed, but it wasn't via email nor lateral movement. It was from a rather unusual source: Microsoft Teams Chat.
We expect Microsoft Teams Chat to be abused more often in the future, so we want to share our learnings with you in this blog. Topics include: how the attack worked, why Microsoft Teams Chat is becoming more popular for criminal groups for ms teams phishing attacks, how to respond to and mitigate these attacks and how your IT team can prevent similar attacks from happening in the future.
NB: Not everything described in this blog may apply to your environment. If you need help, or want to add additional knowledge to this blog, feel free to reach out to our team using the form on this page. For emergencies or anything urgent, please see the incident response page.
Microsoft Teams phishing attack
Microsoft teams phishing is a relatively new threat. It's a topic that TrueSec recently published research on, and was also reported on by Bleeping Computer. Previously, a traditional way to spread malware was via email phishing, but malicious actors found a new way to deliver their malware through the use of Microsoft Teams phishing attacks. They most likely use publicly available tools, such as TeamsPhisher.
The threat actor first compromises a legitimate .onmicrosoft.com domain, which is the mailing domain used for a Microsoft 365 environment for companies without their own custom domain. The actor may also register a completely new tenant. They then change a user account to match the name of a user within the targeted company, usually the CEO. It's via this account that they send automated phishing Teams messages. The victims will see a threat actor isRF trying to chat with them, as shown in Figure 1.
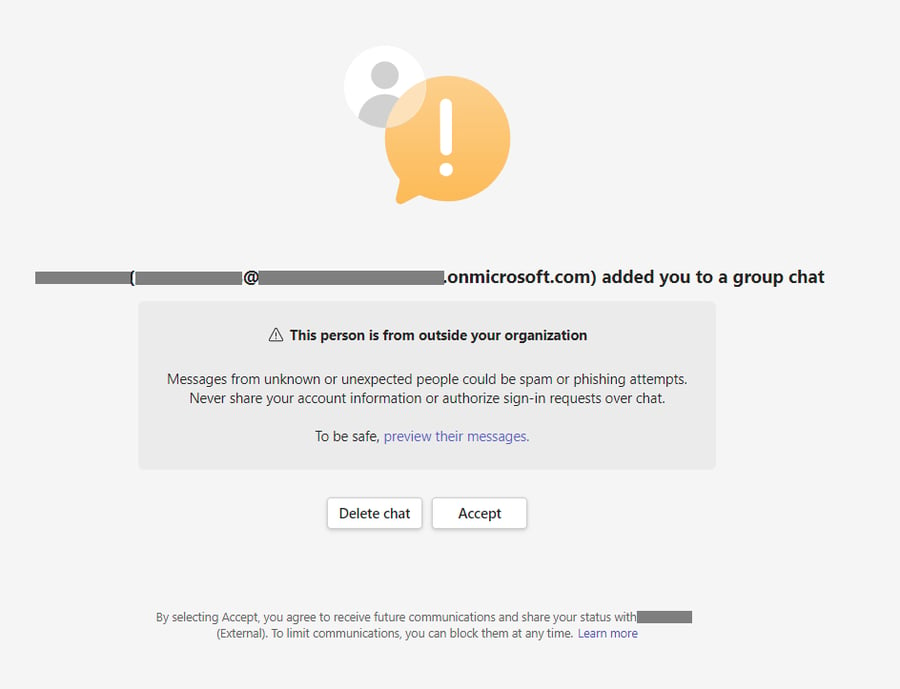
Figure 1. External account trying to chat in Teams
Once the attractive target to accept, an automated message will be returned and the threat actor's account will feature an (External) mark besides the name. We've seen incidents where the message was about a structural reorganisation within the company, indicating that some employees would be fired. An example of such a message can be found in Figure 2. This is of course designed to create fear amongst potential victims, increasing the likelihood that they will open the attached phishing link.
.png?width=673&height=652&name=image%20(1).png)
Figure 2. External account trying to chat in Teams
In some cases we've seen, the message is sent to hundreds of employees and includes phishing links to a Sharepoint site hosting a malicious zip-file. Luckily, both EDR solutions blocked the execution of the malware. We obtained a copy of the malware and did a quick analysis to identify any indicators. We obtained the IP address of the C2 server and recommended the client block it in their firewall for an additional layer of security.
The zip-file contained malicious software called Darkgate Loader, also known as Darkgate malware. When the victim downloads the malicious files (often as ZIP files) and opens it, they will see several files masquerading as a PDF. In reality, these files are LNK files, aimed to trick users to execute a malicious code. A LNK file, or "Link file," is a Windows shortcut that provides quick access to files, folders or programs by storing their location with an associated icon.
Once the user has opened the malicious file, a download of additional malicious software is triggered via the built-in curl.exe command. A legitimate (signed) AutoIt 3 executable is downloaded to the system, along with a malicious AutoIt (au3) script file, which is then executed. The malware will then copy itself to a randomly named directory in C:\ProgramData and add a shortcut with a random name to the Startup folder, to ensure the malware is started every time the user logs in. Figure 3 displays the infection chain of the DarkGate malware.
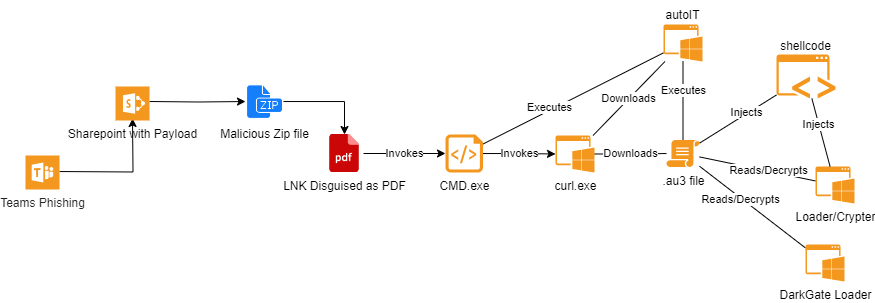
Figure 3. Infection chain DarkGate Loader
Response and mitigation of Phishing Teams Messages
We managed to mitigate such attacks for our customers, however such an attack can still be daunting, especially if hundreds of users are targeted at the same time. If you are faced with a similar threat, we recommend you take the following actions:
1. Communication and end-user awareness
In parallel to the technical measures described below, please make sure to communicate to employees that they have received the malicious Teams External Invite or Teams Chat Message. Share identifiable material, like the impersonated name, email address and screenshots of the attack. Ask employees to delete the chat in the Teams application while IT is handling the response operation. Advise employees to report any suspicious site or activity to IT for further investigation.
Ask end-users who clicked or accepted the invite, to report the event to IT allowing them to investigate employee systems. In the cases we have seen, IT had already deployed EDR on all systems in advance. This allowed us to perform mass threat hunts and scans for indicators of compromise, where end-user feedback only served as confirmation.
2. Use eDiscovery to revoke malicious invites in Purview
Microsoft's eDiscovery dashboard, part of Microsoft Purview (Compliance Centre), allows you to search, investigate and purge (delete) Microsoft Teams messages. Depending on the license, IT can try to retract the malicious invite and/or message via eDiscovery. Detailed instructions on how to delete Microsoft Teams Chats can be found in the documentation provided by Microsoft here.
Please note that you need a Premium eDiscovery license to perform this action. There are no other methods we know of for removing Teams chats from users. Unfortunately, this feature is not included in the Standard Microsoft eDiscovery license. One of our clients had a Premium eDiscovery subscription.
3. Report external domain(s) in Security Centre
Microsoft Security Centre dashboard provides a Report Submission page, where in some cases we've seen, only URLs potentially leading to fraudulent websites, email bodies and email attachments can be submitted for analysis. We reported the malicious “REDACTED-my.sharepoint.com” and “REDACTED.onmicrosoft.com” URL's. Reporting allows Microsoft Security to assess the domains and centrally block them.
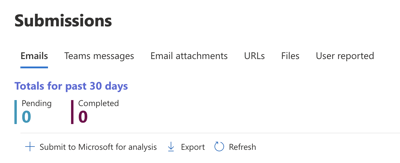
Figure 4
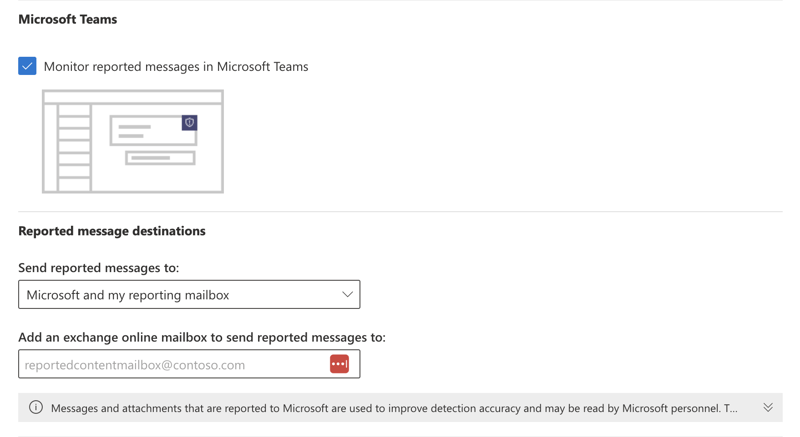
Reporting of Microsoft Teams phishing attacks is only allowed if you explicitly enable this setting first, which allows Teams message reporting by end-users and admins. Our advice is to enable it, if not already enabled. Because changes to this policy takes hours to be rolled-out in your tenant, if the setting is disabled, it will limit your ability to ask end-users to report the Microsoft Teams messages - a scenario we have recently experienced.
Figure 5
4. Block malicious domain(s) in Teams Admin Centre
During an attack, you can block malicious domains in the Microsoft Teams Admin Center (link), preventing incoming messages from malicious actors. To add blocked domains, go to Users -> External Access, as shown in Figure 6.
You have several options: allowlist external domains, denylist external domains, denylist all external domains, or allowlist all external domains, as displayed in Figure 7. Please be aware that changing these settings could impact your business by prohibiting legitimate external users from contacting you via Teams Messages.
While blocking certain domains can be useful, it also means that adversaries could acquire another legitimate .onmicrosoft.com domain and initiate a new attack. Allowing specific external domains might be a better approach to prevent future attacks. However, it would require implementing a process for IT to add trusted domains.
NB: In one case, blocking external access after or during the incident did not purge the invite and/or message that was already sent by a threat actor. It only mitigated the risk of a new invite, new message or next attack with different IoCs.
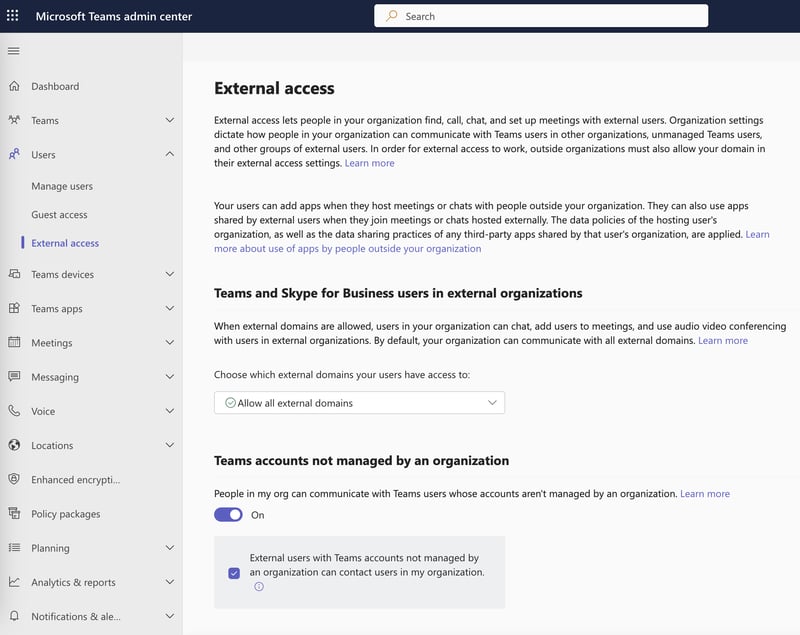
Figure 6
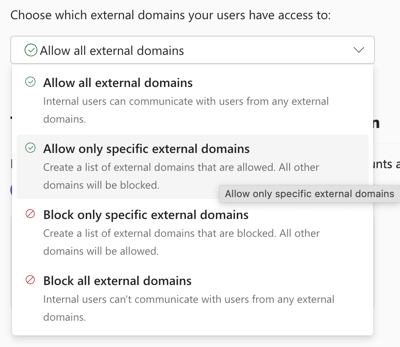
Figure 7
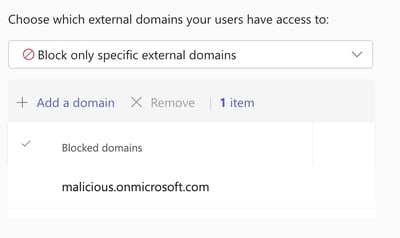
Figure 8
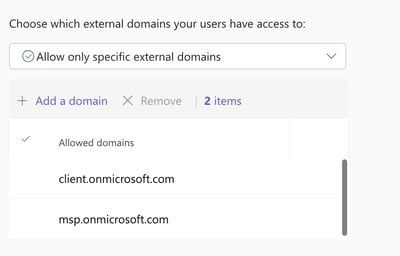
Figure 9
4. Report malicious domain(s) to Microsoft Teams or Microsoft Defender
It is possible to report malicious domains to Microsoft through their MSTC portal, accessible here. The portal is illustrated in Figures 8.
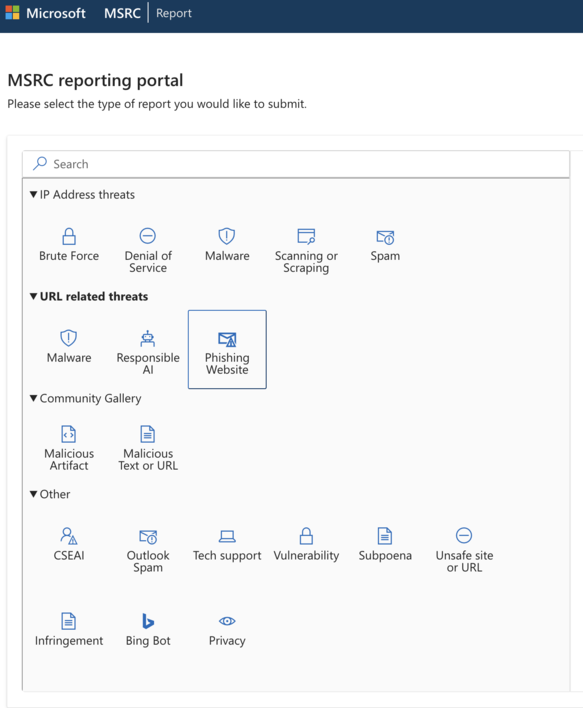
Figure 8
Prevention of phishing attacks and external access
There are ways for companies to protect themselves against phishing lures and identity theft from threat actors. Below are a few measures they could take to protect sensitive data.
1. Change Teams policy to block external domains in teams or whitelist
Setting up a Microsoft Teams policy to allowlisting or denylisting all external communication is a viable measure. If your company relies on external communication, it's advisable to establish an allowlist policy for only trusted domains to send messages to you. However, it's crucial to have a process in place for adding external domains, like the IT support ticketing system used internally.
Tip: eDiscovery Premium can be used to draft a list of benign external domains that are regularly used by the business. This allows you to draft an initial whitelist as a starting point.
2. User awareness/simulation
Since end-users may not yet be familiar with such attacks via Teams or other ‘trusted' internal communication channels, it is critical for companies to raise awareness about suspicious activity. Even in group chat settings within Microsoft Teams, users should be cautious as these can also be targeted by phishing attacks.
In addition to awareness campaigns, it’s also advisable to simulate similar attacks to better prepare your staff. Tools like TeamPhisher can be employed for this purpose. Simulating these attacks allows employees to recognise the signs of phishing lures and helps you strengthen your security measures.
3. Strong EDR configuration and 24/7 follow up
To effectively prevent phishing attacks, it is crucial to have a strong Endpoint Detection and Response (EDR) configuration. This involves:
-
Implementing a robust EDR solution. Choose a reliable EDR solution that can detect and respond to phishing attacks in real-time. Solutions like CrowdStrike Falcon or Microsoft Defender for Endpoint are excellent options.
-
24/7 Follow-up and support. Ensure continuous monitoring and follow-up to quickly identify and mitigate potential threats. Even if an EDR tool blocks a malicious action, human cyber experts should investigate the alert to understand the incident, prevent future occurrences, and remove any remnants of the attack. We've seen EDR tools block malicious actions, but follow-up by a human cyber expert is also necessary. If you leave the alert ‘as is' just because it was blocked, the threat may still exist.
A well-configured EDR solution, combined with vigilant monitoring, is essential for protecting against phishing attacks.
Companies should respond to alerts even if the execution was blocked. It is important to investigate what happened, how it occurred, how to prevent it and how to remove any remnants of the action/infection. In the cases we've seen, the LNK file was executed, but the execution of CMD.exe was blocked on most devices. All devices which have generated an alert were also isolated while we investigated how far the infection had spread.
Indicators of compromise across Teams messages
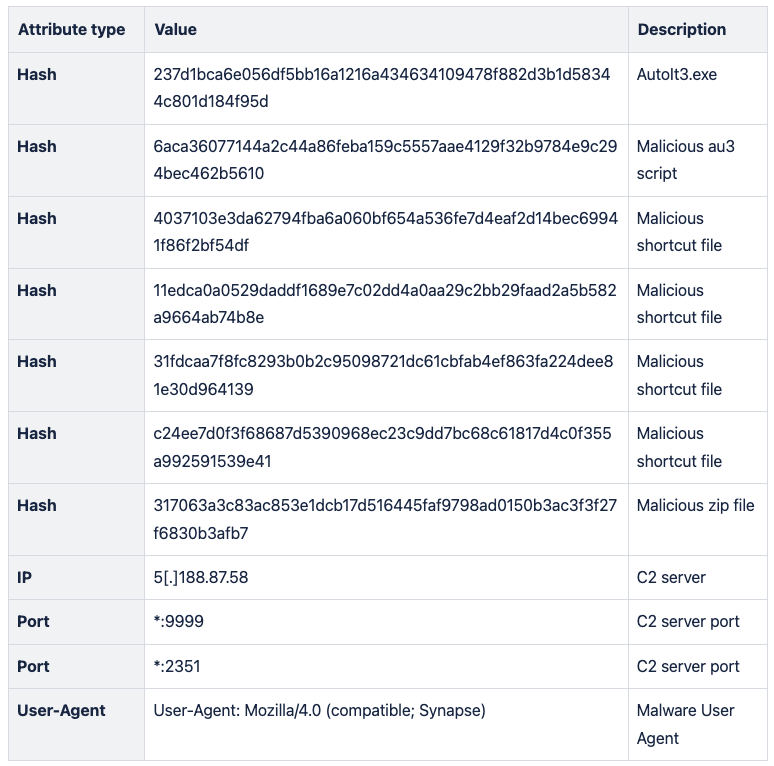
The following list of indicators can be used to prepare your detection systems for a similar attacks on their teams accounts. Please note that these indicators will change over time, relatively quickly. To copy hash values for all elements listed below, you can use this link.
Sample HTTP network traffic of DarkGate:
POST / HTTP/1.0
Host: 5.188.87.58:2351
Keep-Alive: 300
Connection: keep-alive
User-Agent: Mozilla/4.0 (compatible; Synapse)
Content-Type: application/x-www-form-urlencoded
Content-Length: 221
id=REDACTED&data=REDACTED&act=1000
HTTP/1.1 200 OK
Connection: close
Content-Type: text/html; charset=ISO-8859-1
Content-Length: 2
Date: Tue, 12 Sep 2023 17:30:58 GMT16
Malware Hunting
Our sample of DarkGate left traces at the following locations:
C:\Users\<username>\AppData\Local\Temp\Autoit3.exeC:\Users\<username>\AppData\Local\Temp\<random>.au3C:\users\<username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\<random>.lnkC:\ProgramData\<random>\<random>.au3
Queries for incident response
Defender for Endpoint (KQL)
let Hashes = pack_array('237d1bca6e056df5bb16a1216a434634109478f882d3b1d58344c801d184f95d','6aca36077144a2c44a86feba159c5557aae4129f32b9784e9c294bec462b5610','317063a3c83ac853e1dcb17d516445faf9798ad0150b3ac3f3f27f6830b3afb7','4037103e3da62794fba6a060bf654a536fe7d4eaf2d14bec69941f86f2bf54df','11edca0a0529daddf1689e7c02dd4a0aa29c2bb29faad2a5b582a9664ab74b8e','3c470fc007a3c5d59f1c3c483510c60eeb07852905a58d01601bcd0bd2db1245','31fdcaa7f8fc8293b0b2c95098721dc61cbfab4ef863fa224dee81e30d964139','c24ee7d0f3f68687d5390968ec23c9dd7bc68c61817d4c0f355a992591539e41'); |
DeviceFileEvents |
where SHA256 in (Hashes)
DeviceNetworkEvents | where RemoteUrl contains "REDACTED-my.sharepoint.com"
CrowdStrike (Splunk)
main event_simpleName=DnsRequest DomainName="REDACTED-my.sharepoint.com"
| dedup DomainName, ComputerName
| table DomainName, ComputerNameNext steps to prevent social engineering attacks
Social engineering and data breaches are on the rise globally.
Sign up for a demo to find out why European companies trust Eye Security to stop sophisticated cybercriminals.
Conclusion
Phishing is a serious cybercrime that can lead to identity theft and financial losses, among other things. By understanding the various types of phishing attacks and recognising the common features of phishing scams, individuals and organisations can take proactive steps to prevent these threats. Implementing a strong EDR configuration and ensuring 24/7 follow-up are critical measures for detecting and responding to phishing attacks. By taking these precautions, you can safeguard your sensitive data from the ever-evolving tactics of cybercriminals.
FAQ
What is phishing?
Phishing is a type of cybercrime where attackers contact targets via email, telephone, or text message to steal sensitive data. These phishing scams often masquerade as legitimate institutions, tricking individuals into divulging personal details such as banking and credit card information, passwords, and other sensitive data. The consequences of falling for a phishing scam can be severe, leading to identity theft and significant financial loss. By understanding the nature of phishing, individuals and organisations can better protect themselves against these deceptive tactics.
What types of phishing attacks are out there?
Phishing attacks come in various forms, each with its unique approach to deceiving victims:
-
Spear phishing. This targeted phishing attack uses personalised messages to trick specific individuals or organisations into believing the communication is legitimate. By leveraging personal information, attackers increase the likelihood of success.
-
Voice phishing (vishing). Vishing involves using voice over IP (VoIP) to make automated phone calls to large numbers of people. These calls often impersonate financial institutions or other trusted entities to extract sensitive information.
-
SMS phishing (smishing). Smishing uses text messages sent to cell phones or smartphones to deliver bait messages. These messages typically contain links to phishing websites or prompt recipients to share personal details.
-
Man-in-the-Middle phishing. This sophisticated attack employs intermediary tools to intercept communication between the user and a legitimate service, capturing sensitive data without the user’s knowledge.
Understanding these different types of phishing attacks can help individuals and organisations recognise and respond to potential threats more effectively.
What are the most common features of phishing scams?
Phishing scams often exhibit certain characteristics that can help identify them. Being aware of these common features can prevent falling victim to such attacks:
-
Urgent calls to action or threats. Phishing messages often create a sense of urgency, pressuring recipients to act quickly to avoid negative consequences.
-
First-time, infrequent senders, or senders marked [External]. Be cautious of messages from unknown or rarely contacted senders, especially those marked as external.
-
Spelling and bad grammar. Many phishing messages contain spelling errors and poor grammar, which can be a red flag. However, as scammers are increasingly using LLMs to generate phishing campaigns, emails are becoming more sophisticated.
-
Generic greetings. Phishing emails often use generic greetings like “Dear Customer” instead of personalised names.
-
Mismatched email domains. Check the sender’s email domain carefully. Mismatched or unusual domains can indicate a phishing attempt.
-
Outlook banner warnings. Pay attention to banners in Outlook that say, “we could not verify the sender.”
-
Suspicious links or unexpected attachments. Avoid clicking on links or opening attachments from unknown or suspicious sources.
By recognising these features, individuals can better identify and avoid phishing scams.
How can I protect sensitive data?
Fake websites are often used in phishing attacks to deceive users into providing sensitive information. To protect sensitive data, it is crucial to change passwords immediately after a suspected phishing attack. Additionally, users should avoid using the same password across multiple accounts to reduce the risk of compromise.