Introduction
In this article, we'll cover the following:
-
Context on vishing attacks (voice phishing attacks)
-
The details of a real vishing attack combined with social engineering and ransomware that Eye Security prevented for one of its customers
-
Digital forensics and incident response: how we uncovered ransomware traces and rapidly moved to a coordinated defence operation
-
Mitigation and prevention: measures you can put in place to prevent these attacks, including user awareness to spot vishing red flags
-
Threat intelligence and IoC lists
Vishing attacks: context
One factor remains unchanged in the ever-evolving landscape of cyber threats: the unrelenting persistence of ransomware gangs. These digital criminals have honed their technical skills and layered on convincing social engineering tactics to create ever more convincing attacks. The popularity of these tactics has recently increased, as could be seen with the attacks on MGM and Caesars. Vishing scams, a form of voice phishing, are also part of this broader landscape of cyber threats.
The actors behind the ransomware attacks are very resourceful and employ many ways to reach their goals. In this article, we shine a light on the audacious tactics these criminals employ to gain access to mature IT networks, highlighting the disturbing persistence of classic social engineering techniques.
Scammers often target personal details such as account numbers and PINs, using urgency and authority to pressure individuals into revealing this information.
We’ll explore a case where a company, thought to be secure, fell victim to a cunning vishing**attack (voice phishing), resulting in the installation of a ‘backdoor’ to its network. By understanding their methods, we can better prepare our defences to protect ourselves against vishing attacks, ransomware and more.
Social engineering and vishing phone calls: a potent combination
In this specific case, the adversary employed a tactic known as vishing to breach the company by manipulating individuals over the phone into divulging sensitive information. Vishing involves manipulating individuals over the phone to execute potentially harmful actions, often targeting human vulnerabilities instead of technical weaknesses.
In this scenario, the adversary called a company’s retail outlet using a spoofed number, making it appear as though the call came from the company’s headquarters. The attacker (caller) also spoke fluently in our customer’s native language to lower suspicion.
Phone calls are a primary method used in vishing attacks, where scammers impersonate legitimate organizations and exploit psychological pressure to manipulate victims into compliance. The adversary’s goal was to persuade a store employee to visit a compromised OneDrive containing a malicious zip file. When the victim accessed the OneDrive site, the adversary instructed them to download the zip file, extract the contents and execute the Windows shortcut file within the zip file.
From zip file to persistent problem
Here is where it becomes more complex and targeted. The zip file contained a file called CITFIX#29-ERD.lnk (shortcut file) and a folder called ‘extra’. The .lnk appeared to deploy a fix for devices by the manufacturer Citrix. When clicked on, the .lnk, calls a legitimate Microsoft tool called ADExplorer, which is included with the zip, in the extra folder, along with an additional .dll file. The user doesn’t know that ADExplorer is being executed in the background and only sees a message appear in its native language that “Citrix Fix” has been successfully installed.
Attackers often use computer generated voice messages to initiate contact in vishing attacks, creating a sense of trust and manipulating victims into revealing sensitive data. They automate the delivery of messages to potential victims.
What actually happens, by double-clicking the shortcut is:
cmd /c extra\ADExplorer64.exe 16DF573D-988D-4F48-9BAE-66FB6A32F821 F821 && msg %username% Citrix fix #29 is succesfully activated.
Additionally, the attacker used a technique known as ‘dll sideloading’ by abusing the way Windows loads .dlls into processes. Remember the ‘extra’ folder also contained a separate .dll? This ‘version.dll’ gets sideloaded into ADExplorer and is in fact the first stage for a multistage attack chain. After this event, the malicious software creates persistence by copying itself onto the hard drive, and creating a scheduled task. Figure 1 illustrates the attack chain, with EVE representing the adversary.
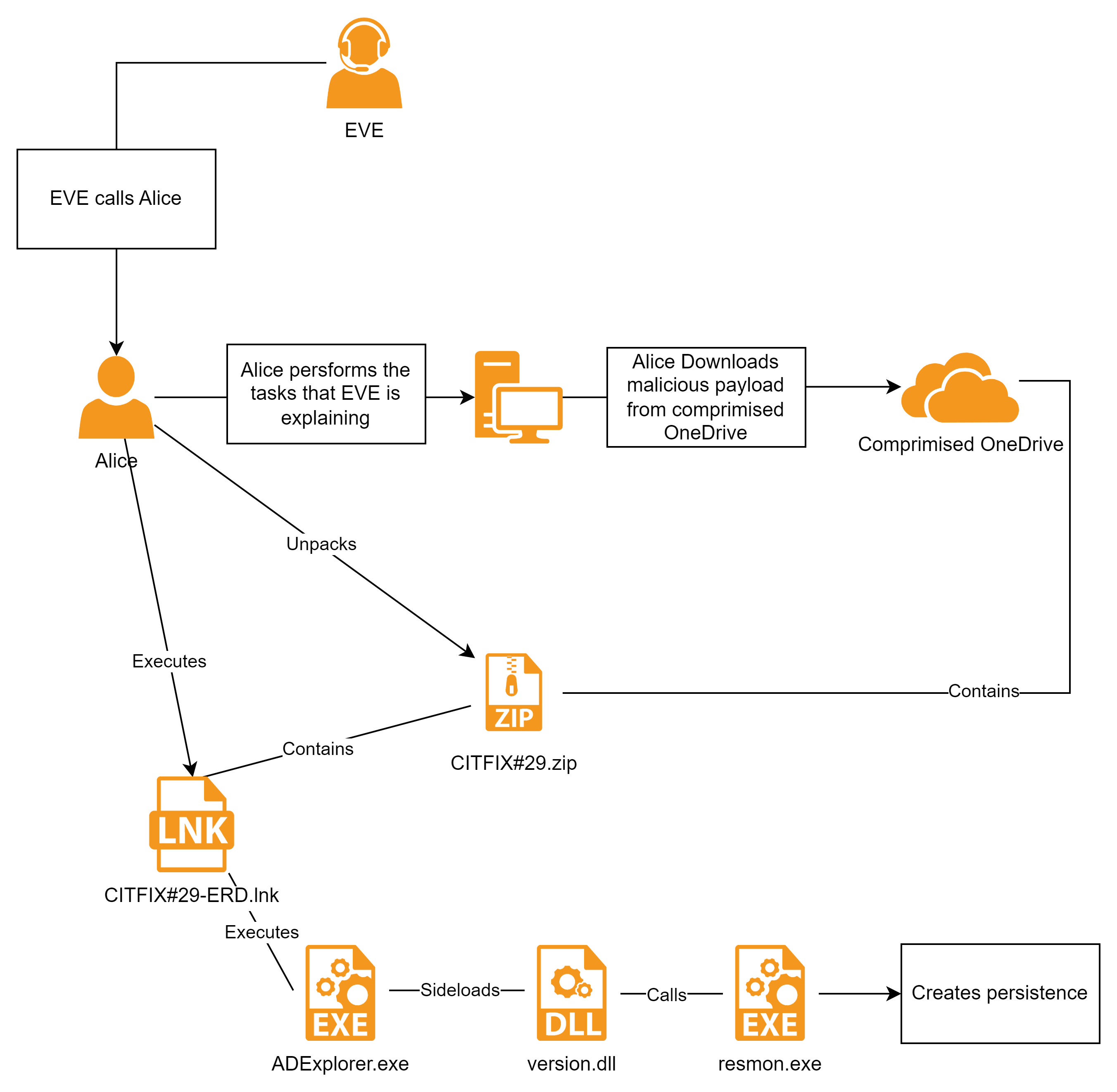
Figure 1
In “Mitigation and prevention: safeguarding your organisation against ransomware and cybercrime”, you will find valuable guidance on how organisations can protect themselves from such attacks.
NB: Not everything described in this blog may apply to your environment. If you need help, or want to add additional knowledge to this blog, feel free to reach out to our team here. For emergencies or anything urgent, please see the incident response page.
Digital forensics and incident response: uncovering ransomware traces with rapid and coordinated defence
For us, it all started with an alert, signalling the potential execution of a suspicious command through WMI (Windows Management Instrumentation). The concerned party contacted our Incident Response team for an investigation. While they believed their existing security solution had blocked the execution, we decided to take active measures to be sure. Victims should also contact their financial institution immediately after discovering a vishing attack to mitigate harm and secure compromised accounts.
To strengthen security measures, we quickly enrolled our own EDR solution and as a precaution, we immediately isolated the affected host from the network. This isolation restricted the machine’s internet access, in case the malware had successfully installed itself on the system.
Subsequently, we retrieved the malicious zip file the victim had downloaded. The zip file was encrypted with a password. The victim could only recall part of the password. We briefly attempted to ‘bruteforce’ the password, but quickly decided to change tack.
That said, we were able to list the contents of the zip file. Among the files, one stood out — ADExplorer.exe, a legitimate tool distributed by Microsoft. With this information, one of our analysts saw an opportunity to extract the contents of the zip file by using a known plaintext attack. By obtaining the original ADExplorer from Microsoft here, the incident responders could execute the following commands to retrieve the same zip file without an encryption:
zip AdExplorer64.zip AdExplorer64.exe
~/pkcrack/bin/extract AdExplorer64.zip AdExplorer64.exe AdExplorer64.plain
~/pkcrack/bin/pkcrack -C ../CITFIX#29.zip -c 'CITFIX#29/extra/ADExplorer64.exe' -p AdExplorer64.plain -d cracked.zip -a
We used the “pkcrack” tool for this part of the operation. Subsequently, a new zip file was created which had the password removed. This zip could be unpacked, which initiated an in-depth analysis of the malware. It became evident that ADExplorer had been employed to sideload the DLL within the zip file the victim downloaded and executed.
At a high level, insights from our malware analysis revealed that the client’s EDR solution had not completely stopped malicious actions. This finding was supported by the remaining signs of persistence on the compromised system and signs of execution of ‘recon’ commands. For instance, the prefetch artefacts clearly showed the execution of whoami.exe, net.exe and tasklist.exe.
As the .dll was heavily obfuscated, we executed the malware in a sandbox and saw that resmon.exe was being started and multiple pieces of shellcode were injected into this process. resmon is a nice target to spawn and inject to, as it appears to be bypassing the antimalware system interface (AMSI) on the Windows. Typically, attackers use perfmon.exe as a shellcode host these days, so seeing resmon is peculiar. By dumping the memory of resmon and using PEsieve, we uncovered an implant, written in C#, which is responsible for communication with the command and control domains (listed in the IOC section). The implant downloads additional payloads as .jpg files from the domains mentioned in the IOC section. These .jpg files are not real pictures, but contain for instance a payload that is executed for further reconnaissance.
PEsieve dumped the C# implants to disk, which allowed us to decompile them with tools such as dnSpy. This revealed yet another layer of obfuscation. By manually going through these files, we learned how the implant downloads, decrypts and executes the jpg payloads from the C2 server. The implant generates a GUID based on several characteristics of the system on which it runs. This is used to fetch the jpg. After decryption using TEA, the reconnaissance payload executes immediately, grabs a screenshot of the desktop and runs commands such as whoami, net and tasklist. Furthermore, it determines if the infected system is part of an Active Directory. If this is the case, it will attempt to query the LDAP server (usually the Domain Controller itself) and retrieves a list of domain administrators and domain computer, all of which are sent to the C2 server. Additional payloads were not observed, but since the attackers can run arbitrary code, anything is possible…
Mitigation and prevention: safeguarding your organisation against vishing attacks, ransomware and cybercrime
1. User awareness to spot vishing red flags and avoid divulging sensitive information
With vishing attacks, as with phishing, we know that humans are the weak spot - most of the time. Similarly to phishing, it’s best practice to create awareness about voice phishing techniques. This can be done by hiring a third party, or to organise sessions with your employees, to discuss how to recognise vishing calls and the implications of such attacks.
Scammers often use a follow up phone call to enhance the credibility of their schemes. By following up a phishing email with a phone call, attackers create a false sense of legitimacy for their malicious intent, making victims more susceptible to deception.
2. Have a policy in place
It is also advisable to establish a policy that employees must adhere to when receiving calls from the IT department. Protecting sensitive information, such as bank account details, is crucial to prevent scams. An authentication policy can help prevent such attacks in the future. Retail outlets, for example, can use the store number to verify, which is usually only known internally. For offices, a staff number can be used. The most common advice is: “If you do not trust it, look up the number yourself (not from the screen!) and call back.”
3. Managed Security Service Provider
As mentioned in previous blogposts, it is important for organisations to have a well-configured EDR solution, such as CrowdStrike Falcon or Defender for Endpoint (P2/Business). These solutions take action when malicious behaviour gets detectied. We have seen EDR tools block malicious actions, but follow-up by a human cyber expert is also necessary, as these tools are not always able to clean up perfectly. If you leave the alert ‘as is’ just because it was blocked, the threat may still exist and some artifacts may remain. In this case, the EDR missed the injection into resmon and the attackers had unfettered access to the system for several hours.
Attackers can also gain access to bank accounts through vishing, manipulating personal information to deplete victims' finances.
Organisations should respond to alerts even if the execution was blocked. It is important to investigate what happened, how it occurred, how to prevent it and how to remove any remnants of the action/infection. This EDR product only cleared the infection afterwards, but leaving the persistance mechanisms in place. This was even worse as the product in place removed evidence and did not stop the threat. We recommend using an EDR solutions which also offers ‘raw’ telemetry, to give analysts additional insights behind the fact.
4. Access control
Tools like AppLocker can prevent end-users from executing programs without admin credentials. This provides an extra measure, since the adversary needs admin credentials to install his backdoor through vishing.
It's also crucial to protect your social security number, as scammers often request this sensitive information to manipulate individuals or resolve issues without escalation.
Threat intelligence and IoC lists: the power of proactive defence
# IoC
| Attribute type | Value | Description |
|----------------|-------|-------------|
| Hash | 3ac2d170eeefd5d866ca2285da2a7387c544250d6978bab621c2a80b95946712 | Malicious zip file |
| Hash | 816e0c0a8236d0f929069fe9085bb483e5b881053e12c64dc1a50ee5638d0160 | Malicious shortcut file |
| Hash | be98288b9d540e449eee39963269c2b4ce0d54b7b1d3f322dedce157a837a209 | Malicious DLL file |
| Hash | e451287843b3927c6046eaabd3e22b929bc1f445eec23a73b1398b115d02e4fb | ADExplorer.exe |
| DNS | acpbt[.]com | C2 domain |
| DNS | blacksprutmarket24[.]com | C2 domain |
| DNS | byoczv[.]com | C2 domain |
| DNS | distributiongl[.]com | C2 domain |
| DNS | funcadia[.]com | C2 domain |
| DNS | inlade[.]com | C2 domain |
| DNS | pknluttelgeest[.]nl | C2 domain |
| DNS | z9x[.]org | C2 domain |
| IPv4 | 185.130.47[.]139 | C2 IP address |
| IPv4 | 185.130.47[.]143 | C2 IP address |
| IPv4 | 185.130.47[.]154 | C2 IP address |
| IPv4 | 185.130.47[.]185 | C2 IP address |
| IPv4 | 185.130.47[.]210 | C2 IP address |
| IPv4 | 185.130.47[.]72 | C2 IP address |
# Hunting
1. `C:\Users\<username>\AppData\Roaming\Microsoft\ADE`
2. `C:\ProgramData\Microsoft\ADE`
Conclusion and next steps
We hope this gives you enough information to get started.
If you want help with any aspect of your cyber security, please reach out to us directly.
FAQ
What is vishing?
Vishing, also known as voice phishing, is a type of social engineering attack that uses phone calls or voice messages to trick victims into revealing sensitive information, such as bank account details, login credentials, or personal identification information (PII). Vishing attacks aim to manipulate individuals into divulging confidential information, which can lead to financial loss, identity theft, or other malicious activities. These attacks often exploit human psychology, creating a sense of urgency or trust to persuade victims to share their sensitive information. A phishing attack, including vishing, can lead to significant data breaches if not promptly addressed.
How do vishing attacks work?
Vishing attacks typically involve a combination of social engineering tactics and technology to trick victims into revealing sensitive information. Understanding the mechanics of these attacks can help individuals and organizations better protect themselves.
What techniques are used in vishing attacks?
-
Pretexting: Scammers create a fabricated story or “pretext” to justify the call and gain the victim’s trust. This could involve pretending to be a bank representative, a tech support agent, or a delivery service employee.
-
Caller ID spoofing: Scammers manipulate caller ID information to make it appear as though the call is coming from a legitimate source, such as a bank or government agency.
-
Urgency tactics: Scammers create a sense of urgency to pressure victims into taking action without thinking critically or verifying the caller’s identity. They might claim that immediate action is needed to prevent fraud or resolve an issue.
-
Voice phishing: Scammers use voice messages or phone calls to trick victims into revealing sensitive information. These calls often sound professional and convincing, making it difficult for victims to recognize the scam.
-
Remote access: Scammers convince victims to grant remote access to their devices, allowing them to install malware or steal sensitive information. This is often done under the guise of providing technical support or resolving an issue.
By understanding how vishing attacks work and the techniques used by scammers, individuals and companies can take steps to prevent these types of attacks and protect their sensitive information.



