We want to bring your attention to a critical vulnerability in GeoServer that has recently become relevant again, as an easy-to-use hacking tool has been published hours ago. As this critical vulnerability has now been weaponised, it directly poses a significant risk to organisations that have not yet applied the necessary patches of last February. Municipalities, universities, and various other institutions are among the list of vulnerable organisations.
Our top priority is the safety of our clients. That's why our Threat Intelligence team has informed our clients this morning about specific vulnerable hosts, utilising endpoint data and online vulnerability scans of their attack surface.
The impact of this vulnerability extends beyond the potential for ransomware attacks. While the risk of ransomware remains limited, there is a higher chance of data leakage, credential harvesting, and website defacement, which can significantly damage your organisation's reputation.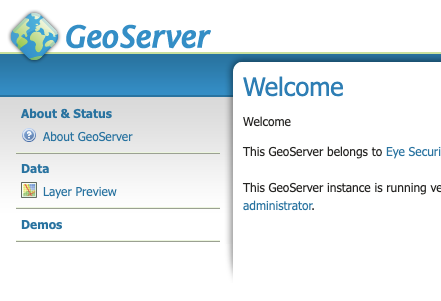
To ensure the security of your GeoServer server, we urge you to take immediate action. Follow these steps:
- Identify if you have GeoServer running in your organisation and check its version. You can check the version by visiting the public landing page of GeoServer and look for “This GeoServer Instance is running version […]”.
- All versions below 2.21.4 (for 2.21.x range) or 2.22.2 (for 2.22.x range) are vulnerable.
- So for example, version 2.21.2 is vulnerable as it is below 2.21.4 and patching is crucial. This vulnerability can lead to remote code execution, allowing unauthorized users to exploit the system through multiple OGC request parameters, which can realize remote code execution.
- If your server is running a vulnerable version, promptly apply the available patch provided since February 2023. Addressing this vulnerability is crucial to maintaining GeoServer functionality and preventing potential deployment failures.
- Visit https://geoserver.org/download/ for the appropriate instructions of GeoServer and review their documentation via https://docs.geoserver.org/stable/en/user/installation/upgrade.html. Updating to secure versions is essential to mitigate the risk of remote code execution and other security vulnerabilities.
- If patching is not feasible immediately, consider taking down the server temporarily to minimise the risk of exploitation, or consider closing off internet access via the edge firewall.
Running outdated versions of GeoServer can expose your system to vulnerable code, which can be exploited through various means, including the Web Map Service (WMS). Ensuring your software is up-to-date is critical to maintaining security.
We understand the importance of safeguarding your data and systems. Therefore, we strongly recommend addressing this vulnerability as soon as possible to prevent potential security breaches.
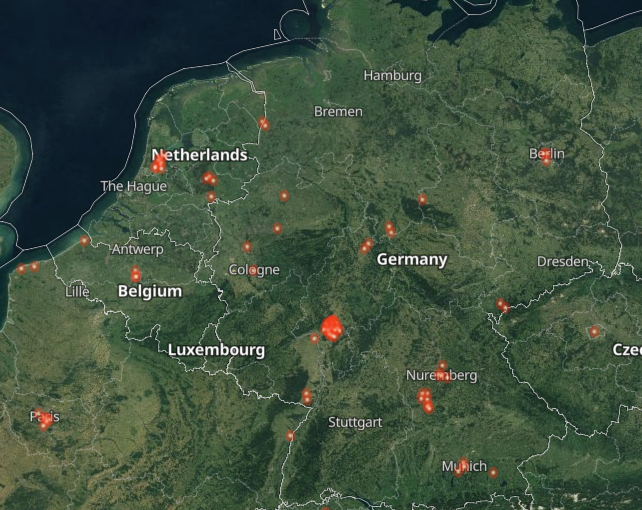
Vulnerable organisations in The Netherlands, Germany and Belgium
For more information and technical details about the vulnerability, you can refer to the following resources:
- Hacking tool: GitHub - GeoServer Hacking Tool
- Official CVE (February): CVE-2023-25157 - Common Vulnerabilities and Exposures
Take action today to protect your GeoServer server and ensure the safety of your organisation's data. If you have any questions or need assistance, feel free to reach out to our team.




