We have all been there: starting a new job can be very overwhelming. There are new systems that you have to get to know, new colleagues whose names you don't know yet and you receive a lot of practical information about the company. After a tiring day of meeting your new colleagues and drinking lots of coffee you’ll have to log in to your laptop for the first time, using new applications and choosing new login credentials for all the applications that you will be working with. A perfect time to send a phishing email that induces you to enter your password on a rogue site! The fact that the mail was sent from a completely different domain than your company actually uses, and that Karen Smits is not a direct colleague of yours at all, are quickly overlooked...
A psychological game
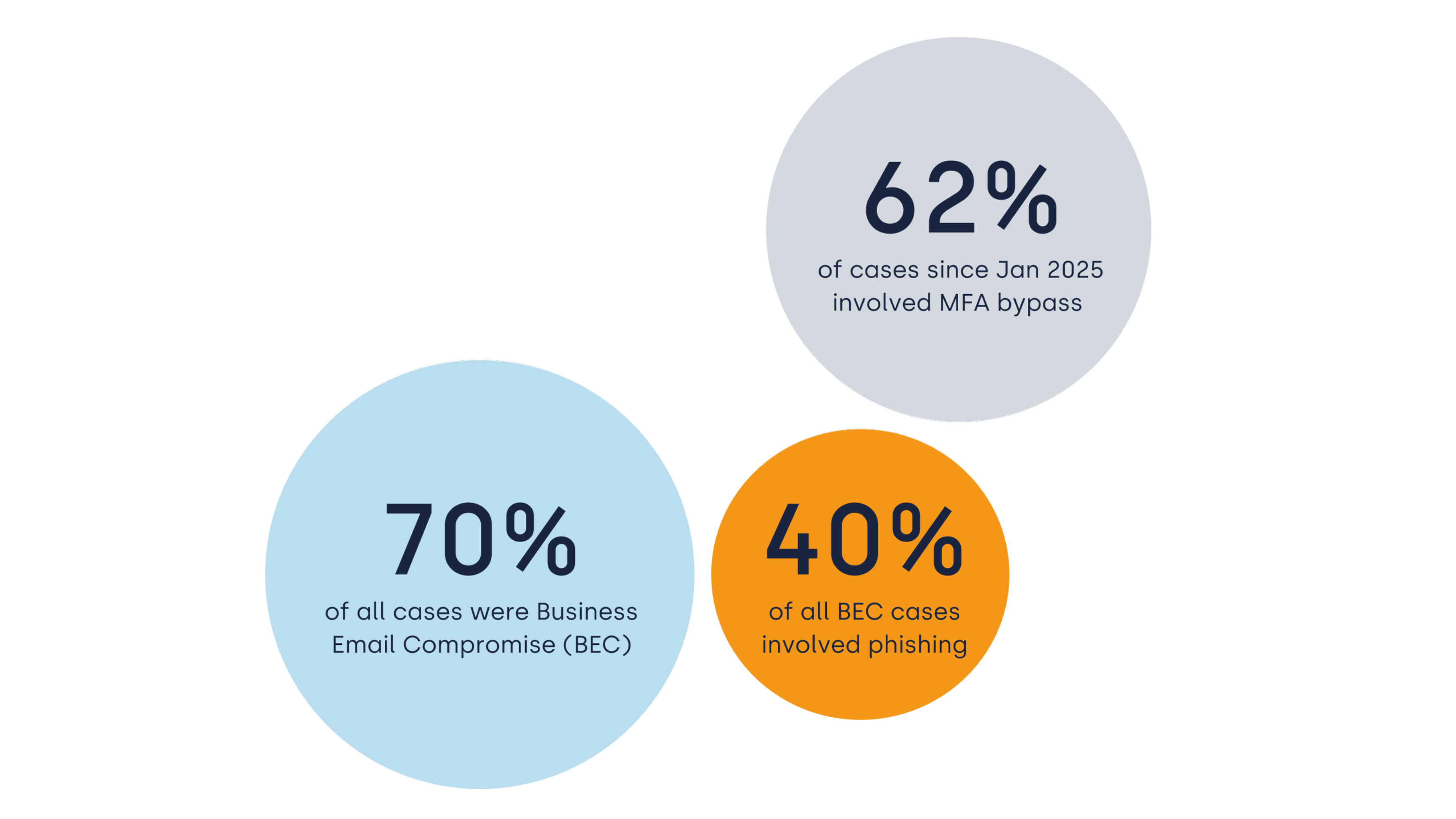
Phishing is a well-known way of extracting information from an unwitting victim. Deception induces the victim to enter information such as login details on a website that is controlled by the attacker. The data can be used to log into the victim's account and then access other users' computer systems, files, or accounts.
Method
Nowadays, you will find a lot of information about someone online. A criminal can find who your current employer is easily on your LinkedIn profile. They use this kind of information as input for phishing emails. In addition, this information can be used to identify new employees by monitoring a company's employee list. Finding out the email address of a new employee is not difficult: the structure (eg initial.lastname@domain.com) of email addresses can often be found via a company's website, for example on the 'contact' page or in blog posts.
Sending a phishing e-mail has a high chance of success, especially with new employees. It is logical that as a new employee you must log in to all kinds of services for the first time and you do not yet know all the names and positions of colleagues. This makes it easier for attackers to compose an email that appears legitimate. Correlating information via public information and 'educated guessing' creates an email that is difficult for new employees to distinguish from legitimate. For example, new employees will most likely not notice that the contact person from the email works in a completely different department of the company.
Measures
There are several measures that make phishing more difficult:
- Specifically for new employees, it is important to make cyber security awareness part of the onboarding process. In doing so, address questions such as: How is communication within the company? Who can you contact if you are not sure whether a certain email is a phishing email? What should you do if you think you have entered your details on a site that cannot be trusted? What are the measures that the company has put in place to combat cyber security incidents?
- Furthermore, it is important to set up Multi-Factor Authentication (MFA) for all users. This means that in addition to a password, you also need a code from your phone to log in, for example. This makes it much more difficult for malicious parties to hack an account, because a second step is always required in addition to the password.
- Use a password manager. As a result, an extra step is required to enter credentials on a rogue website, while it is not necessary on the legitimate website.
- Technical: show users a warning with every email sent from outside the organisation. For Microsoft 365 users, this can be set through Microsoft Exchange. Combine this with a DMARC policy that ensures that malicious parties cannot email on behalf of the company.
Conclusion
Be aware of what information can be found online about people, and what malicious parties can use it for. Make cyber security awareness part of the onboarding of new employees and provide regular training and anti-phishing campaigns. Do you have questions about this topic? Or do you need assistance in getting the cyber security culture in order within your company? Please email us at info@eye.security.