Blogs.
Product Update: Vulnerability & Threat Hunting
In this blog, we interview Robbin Begeer, Product Manager at Eye Security,...
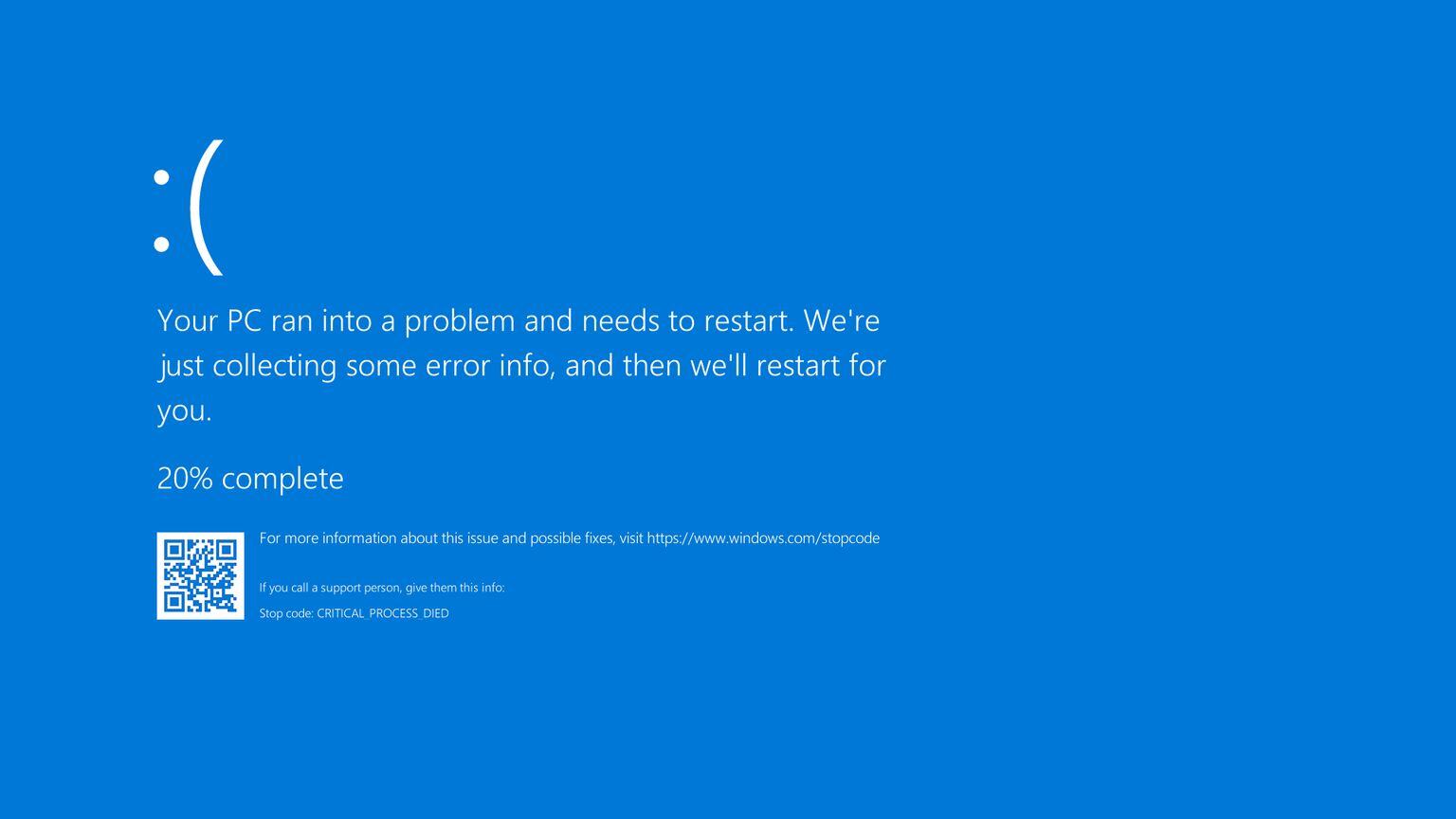
CrowdStrike Falcon and Microsoft blue screen issue updates
Last updated: July 30th at 00:00 CEST In this blog, we provided real-time...


NIS2 Directive Overview: In-depth look at Articles 21 and 23
While many EU countries are still working out the specifics of implementing the...

NIS2: How the New EU Cyber Law Protects Your Business
Cyber attacks are now big business – but they’re impacting smaller companies....


NIS2 EU: Top 3 Cyber Laws and Their High-Level Definitions
Cybersecurity compliance can seem daunting. With so many new regulations coming...

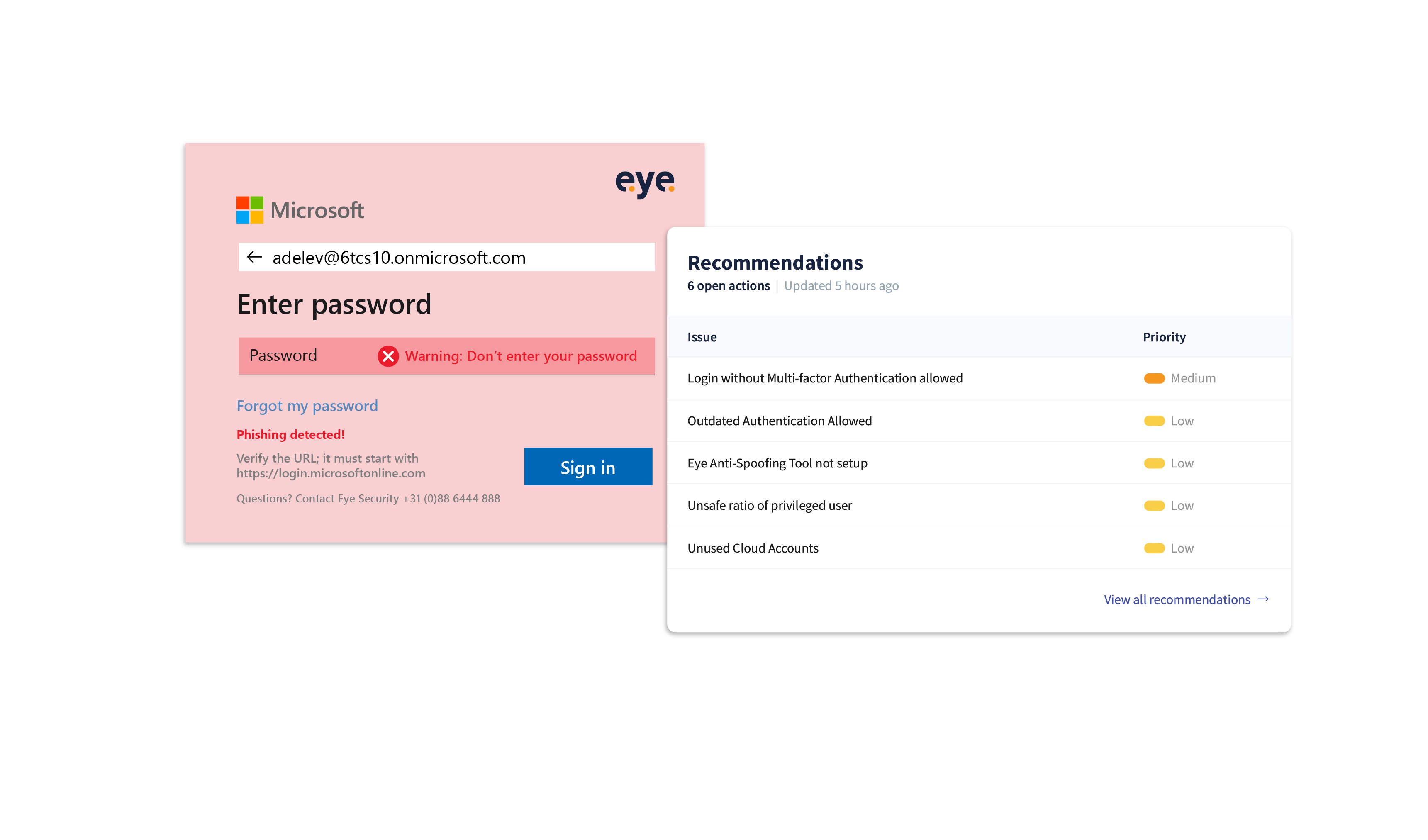
Empowering security: the battle against Login Spoofing
Introduction Battling cyber-crime can sometimes feel like an endless tennis...
A Conti-nuous issue
Introduction In this blog, we shed light on our findings during a forensic...


A case of ransomware, resolved
...

Logistics cybersecurity in 2024: Hello new growth! Hello new risks...
Sustainability. Growth. Digitalisation. These are the words everyone's using...
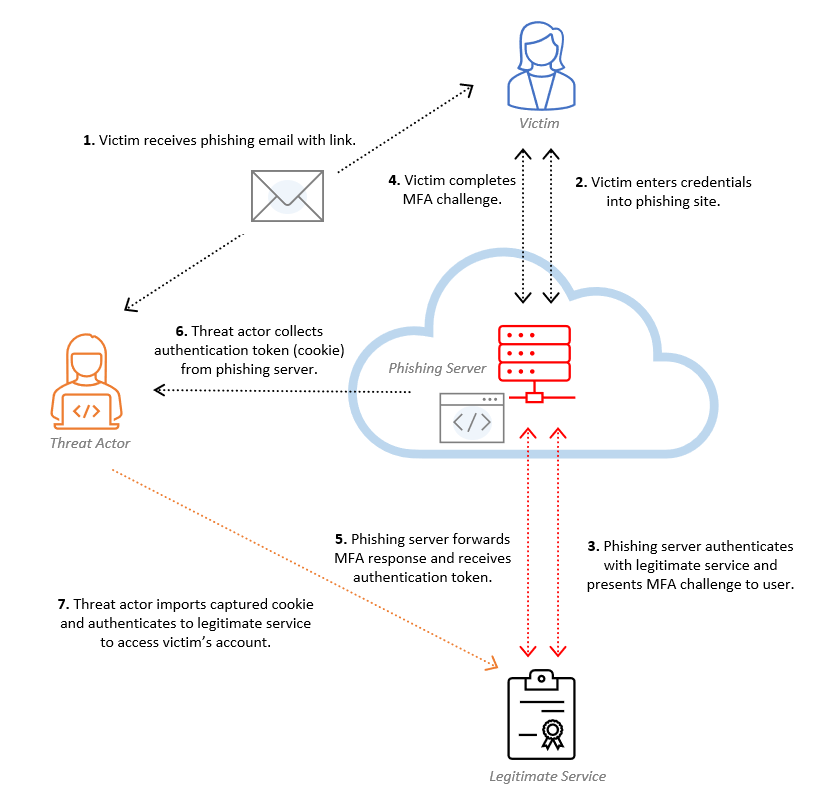
How to defend against EvilProxy when a phishing attack strikes
Here at Eye Security, we have observed a disturbing increase in security...

