Blogs.

The story of a real vishing attack: detailed incident walkthrough
Introduction In this article, we'll cover the following: Context on vishing...

Mitigating Cyber Threats with Risk Intelligence
What is Risk Intelligence - and how can it help you? Business leaders...


Hunting for You and Eye #1
Eye Security's ongoing hunt for cyber threats provides valuable insights into...

Security Alert: Critical Geoserver Vulnerabilities
We want to bring your attention to a critical vulnerability in GeoServer that...


What is the chance of getting hacked? Eye Security: 1 in 5
In recent years, we have seen an increasing number of cyber attacks on...

6 Cybersecurity Resolutions for 2023 – And How to Implement Them
The new year is a good opportunity for companies to break bad habits -- such as...
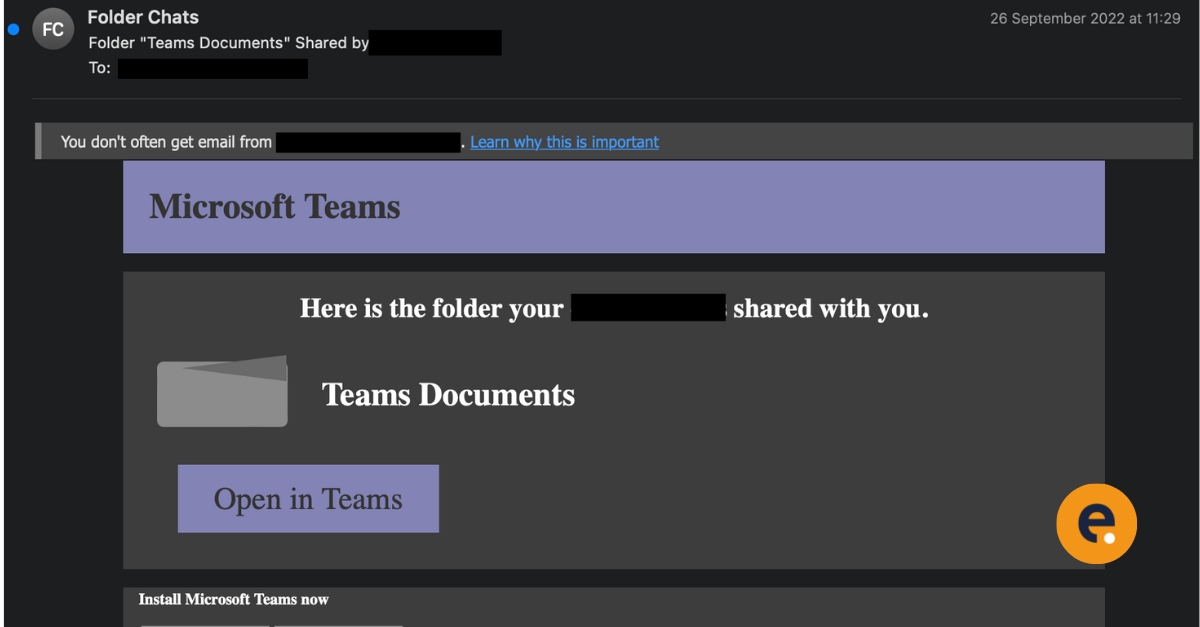
Large scale phishing campaign quickly utilises Legacy Authentication before Microsoft disables it
Security Specialists from Eye Security have observed a rather large phishing...
WinRS and Exchange, a sneaky backdoor
How it started ? On the 10th of May around lunch, our Security Operation Centre...

Are new employees the weakest link in your organisation?
We have all been there: starting a new job can be very overwhelming. There are...


Log4j Critical Updates by Eye CERT
Introduction Attackers are actively exploiting a remote code execution...
