Blogs.

The silent crisis: IT burnout due to increased cybercrime
Employee absenteeism is rising among IT managers and employees, as are burnout...

NIS2: how will it be transposed in European countries?
The NIS2 Directive is the latest European cybersecurity regulation, aiming to...

European Union working on new security directive
The impact of the new 'cybersecurity' directive, NIS2, on insurers Although the...

Cyber insurance: your safety net in an increasingly risky world
To minimise the impact of a cyber incident, preventive security measures must...

What is the chance of getting hacked? Eye Security: 1 in 5
In recent years, we have seen an increasing number of cyber attacks on...

6 Cybersecurity Resolutions for 2023 – And How to Implement Them
The new year is a good opportunity for companies to break bad habits -- such as...

Antivirus is not enough to protect your business - here is why
Many antivirus software providers claim that their product will protect you...
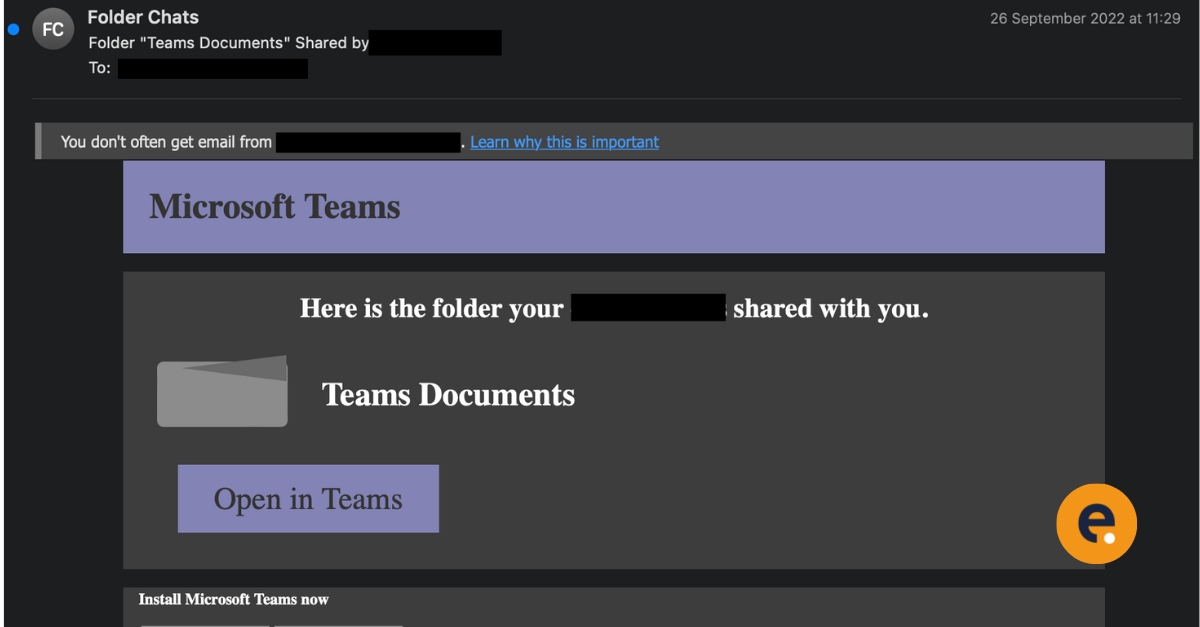
Large scale phishing campaign quickly utilises Legacy Authentication before Microsoft disables it
Security Specialists from Eye Security have observed a rather large phishing...

Log4j Critical Updates by Eye CERT
Introduction Attackers are actively exploiting a remote code execution...

5 tips to secure your company for free
No matter how big or small your company is, everyone has crown jewels: crucial...
