Blogs.
Read our blogs for the latest cyber security updates.
Filter
#}
Search
4 min read
Brute Force Attack on SSLVPN Leads to Stealthy Network Intrusion
Attacks do not always start with malware or flashy exploits. Sometimes, all it...
By:
Eye Security
8 min read
Retail Giants Breached: What the M&S, Harrods & UNFI Attacks Mean for Your Cyber Defences
A surge of high-impact cyberattacks is shaking the retail sector, exposing...
By:
Eye Security

5 min read
Top 5 Cyber Threats Manufacturers Face in 2025
Cyber attacks can be devastating to manufacturers. They disrupt supply chains,...
By:
Eye Security
9 min read
Manufacturing and Cybersecurity: What Are the Challenges?
Manufacturing companies form the very foundation of the global economy....
By:
Eye Security
6 min read
A new paradigm to extinguish cyber risk for good: 24/7 protection connects with cyber insurance
...
By:
Eye Security

2 min read
Eliminating cyber risk for your clients together
Businesses built on partnership In the relatively short time we’ve been in...
By:
Eye Security
6 min read
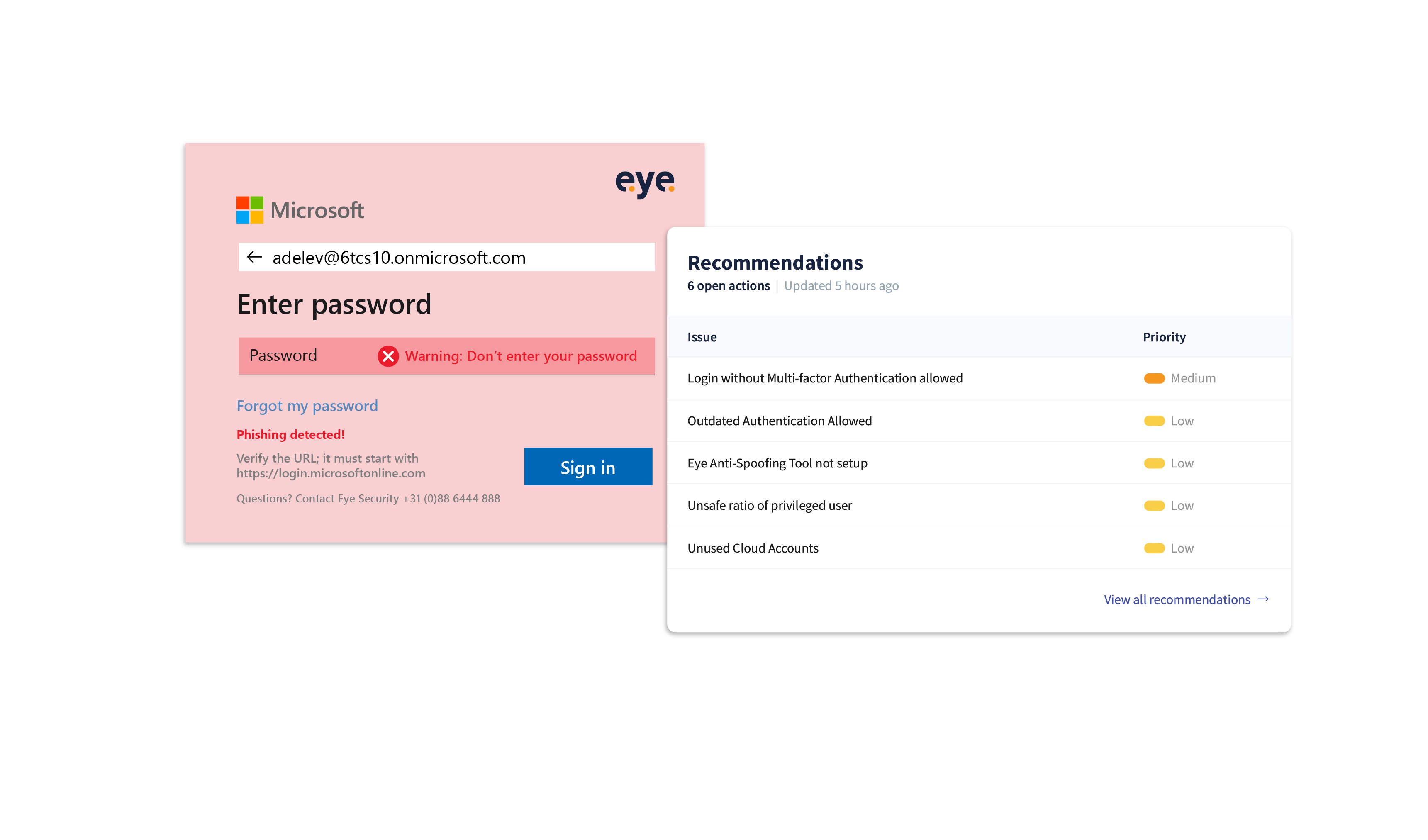
Empowering security: the battle against Login Spoofing
Introduction Battling cyber-crime can sometimes feel like an endless tennis...
By:
Eye Security

1 min read
A case of ransomware, resolved
...
By:
Eye Security

4 min read
Logistics cybersecurity in 2024: Hello new growth! Hello new risks...
Sustainability. Growth. Digitalisation. These are the words everyone's using...
By:
Eye Security
9 min read
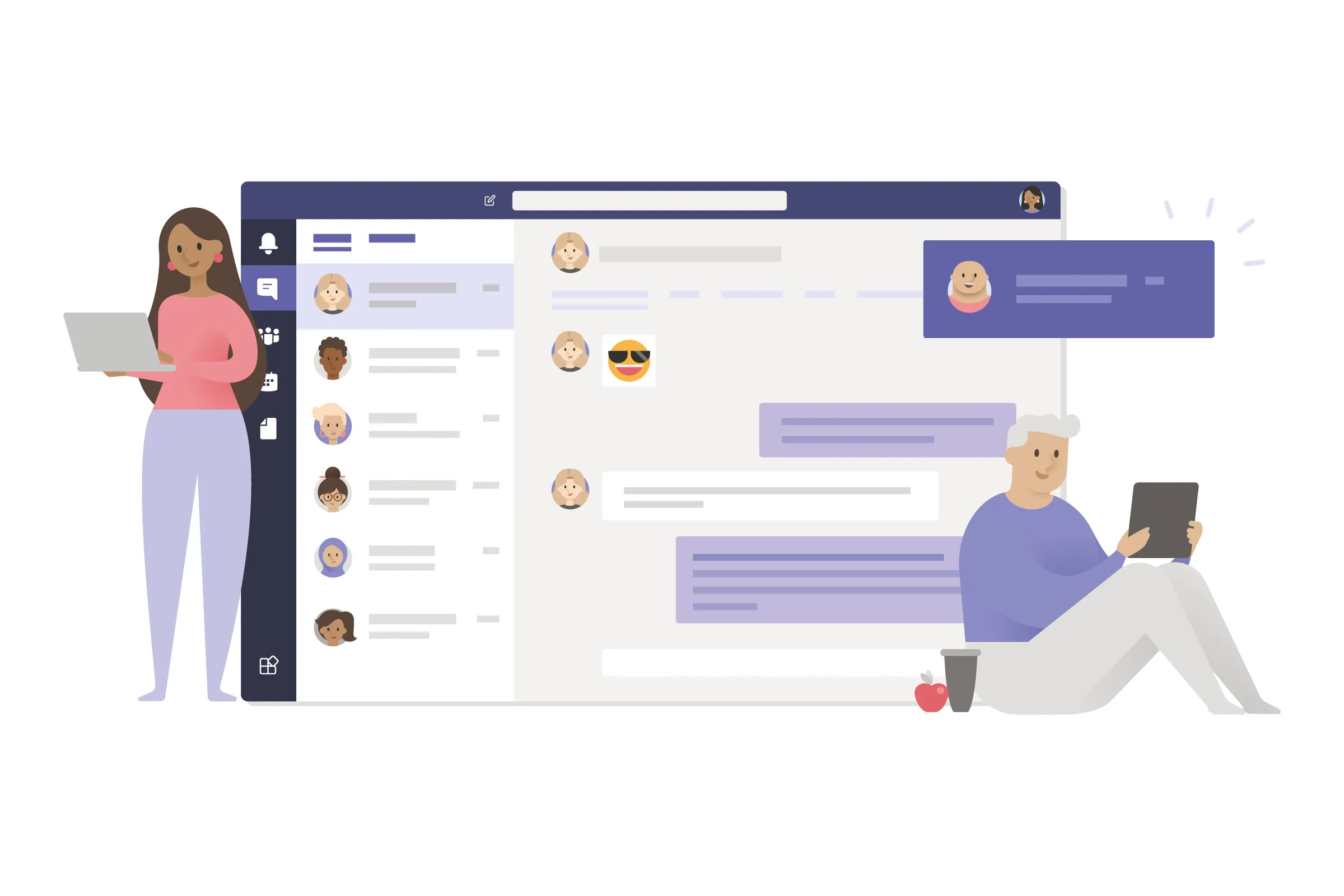
Microsoft Teams Phishing: How to Stop The Rising Phishing Threat
Introduction Around mid-September, our Security Operations Centre (SOC)...
By:
Eye Security
